Blog
A home for my posts about infosec.
2022
Plugins for Persistence
Using code editor plugins for persistence. Continue reading Plugins for Persistence
2021

Auto(It)mating your .NET Tradecraft
AutoIt, .NET and Windows protection bypasses. Continue reading Auto(It)mating your .NET Tradecraft

Pillaging Password Managers with UI automation
Using UI automation & keystrokes to extract credentials from password manager vaults. Continue reading Pillaging Password Managers with UI automation

Operating with AutoIt
AutoIt for offsec assessments. Continue reading Operating with AutoIt
2020

Retrieving Data from Thunderbird and Firefox
Extracting sensitive information from Mozilla apps. Continue reading Retrieving Data from Thunderbird and Firefox
2018

A Data Hunting Overview
A guide to data hunting during engagements. Continue reading A Data Hunting Overview

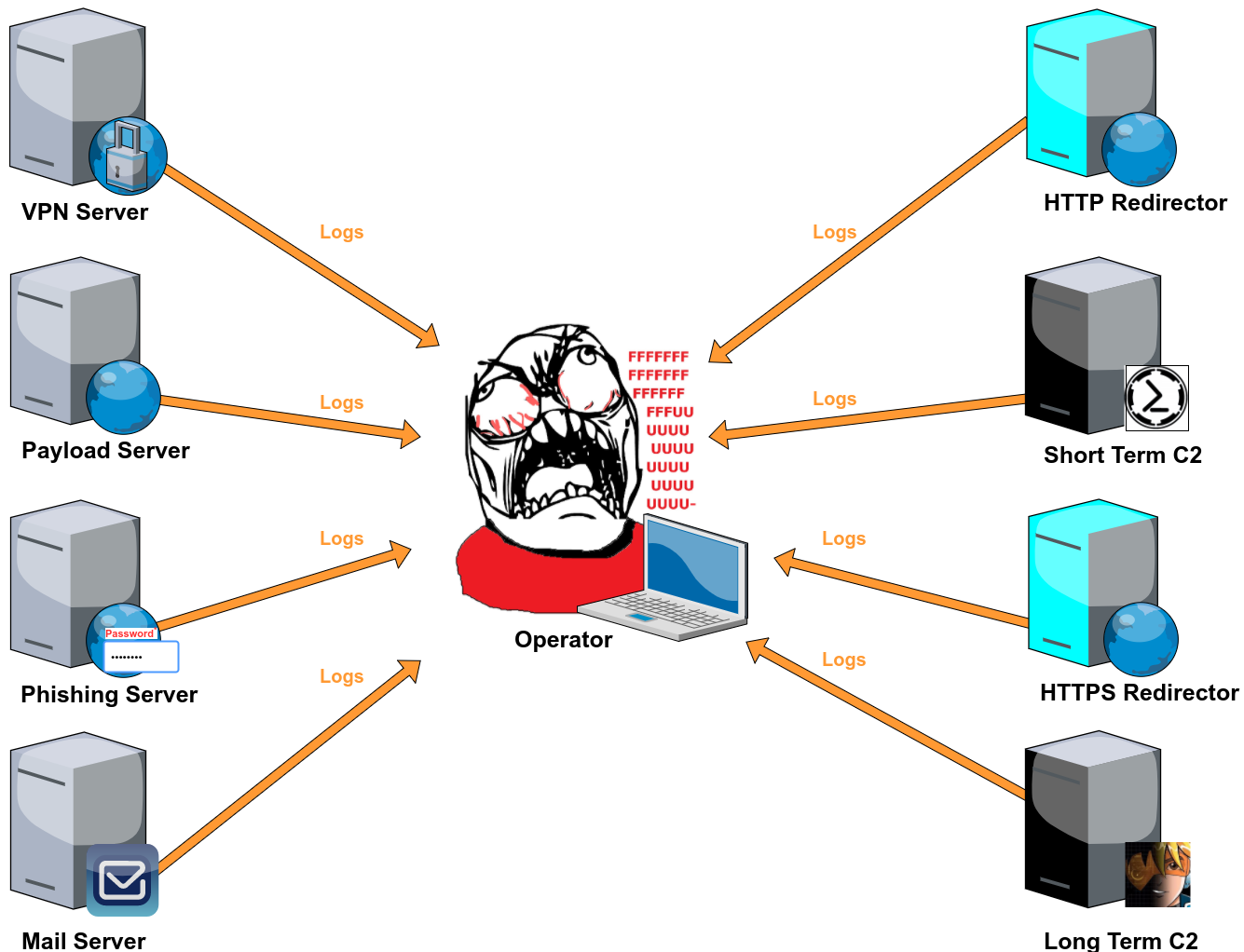
Attack Infrastructure Logging - Part 4 - Log Event Alerting
Slack alerting in Graylog2. Continue reading Attack Infrastructure Logging - Part 4 - Log Event Alerting
Attack Infrastructure Logging - Part 3 - Graylog Dashboard
Setting up a Graylog2 dashboard. Continue reading Attack Infrastructure Logging - Part 3 - Graylog Dashboard
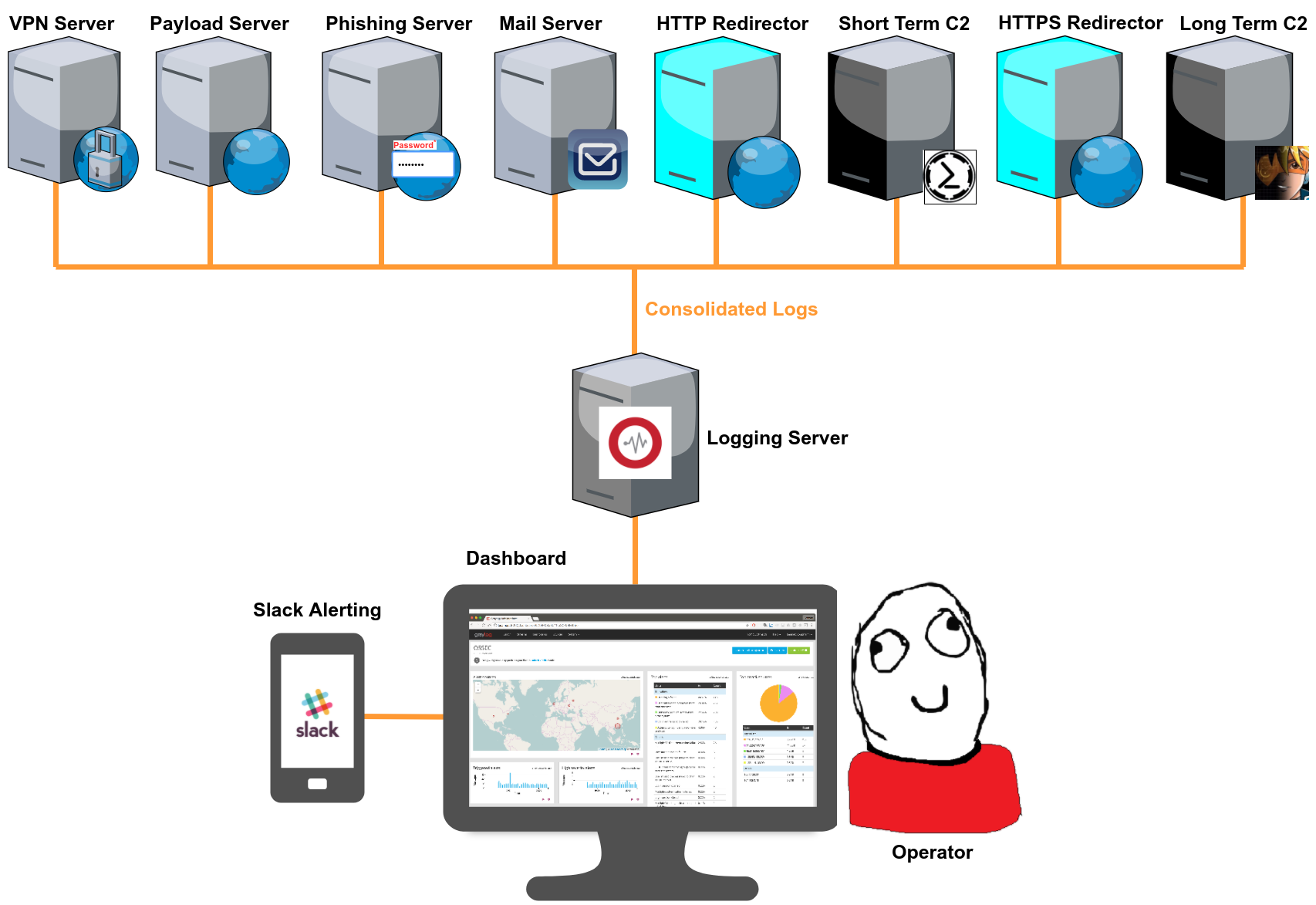
Attack Infrastructure Logging - Part 2 - Log Aggregation
Configuring log aggregation in Graylog2. Continue reading Attack Infrastructure Logging - Part 2 - Log Aggregation
2017
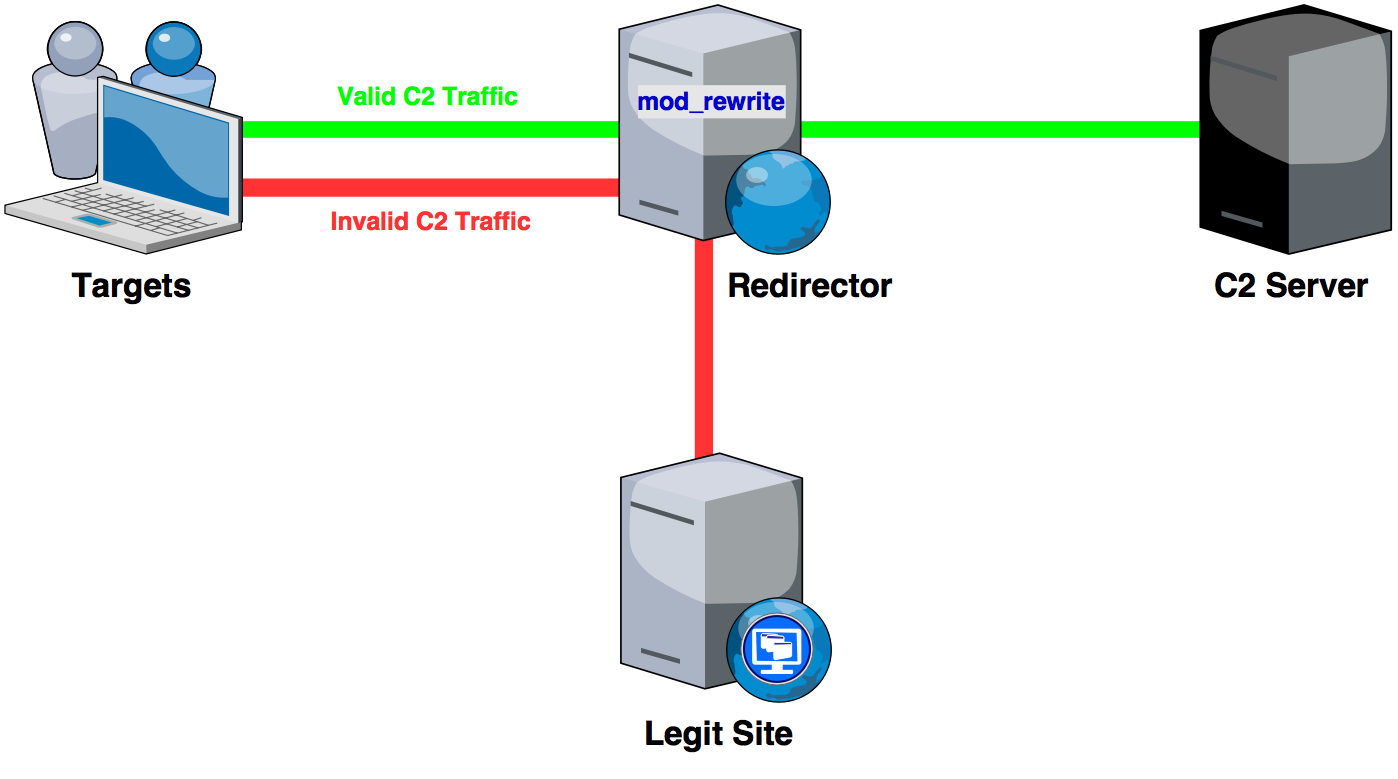
Securing your Empire C2 with Apache mod_rewrite
HTTP C2 redirection with Empire and mod_rewrite. Continue reading Securing your Empire C2 with Apache mod_rewrite

Abusing SolarWinds Network Performance Monitor for Post-Exploitation
Windows post-exploitation with SolarWinds NPM. Continue reading Abusing SolarWinds Network Performance Monitor for Post-Exploitation

AIX for Penetration Testers
AIX enumeration guide for penetration testers. Continue reading AIX for Penetration Testers
2016
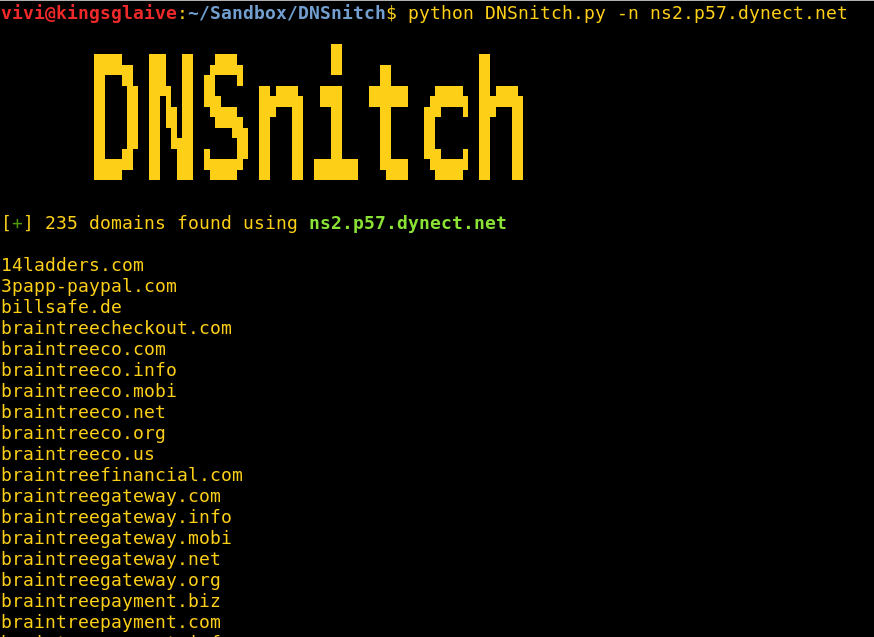
DNSnitch - Reverse NS Lookups & Zone Transfers
Reverse NS Lookups & Zone Transfers. Continue reading DNSnitch - Reverse NS Lookups & Zone Transfers

WiFi Social Engineering
Messing around with Wifiphisher. Continue reading WiFi Social Engineering